Setting up
Downloading Nessus Essentials
Snapshot To Save Space Or Incase Of Errors
This Lab builds on top of the Active Directory Lab. I recommend taking a snapshot of the Windows 10 Client before installing Nessus in case you encounter any errors or if you want to save space, you can note down the found vulnerabilities after completing this lab and restore back to the snapshot to save space for future labs that will keep building on top.
Lab Brief Summary
The overall lab is to get used to using the Nessus vulnerability scanner and seeing the differences in the findings after each scan performed.
In this lab we will perform a non-credentialed scan, followed by a credentialed scan, then a second credentialed scan after downloading deprecated software, then finally remediating any critical and high-ranking Vulnerabilities found.
Nessus Registration and Download
Use this link inside of the Windows 10 Client.
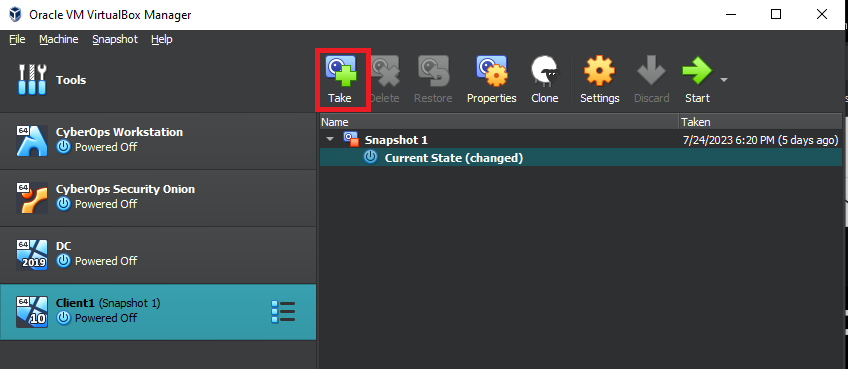
To make a snapshot, simply click on the “Take” button as shown below. Make sure that the Windows 10 Client is Highlighted. If you ever need to use the snapshot, just click on “Snapshot 1” and the “Restore” button will be available to use.
Inside of Windows 10 Virtual Machine, I logged in with the “a-vcoil” account which is the domain admin account that we created in the Active Directory Lab.
Once inside, navigate to the URL that is up above to register and download Nessus Essentials. You’ll have to put in your First and last name as well as an email address. Once you plug those in, there should be a button that appears to download Nessus. An email will also be sent to you with your activation code. There should also be a download button inside of that email.
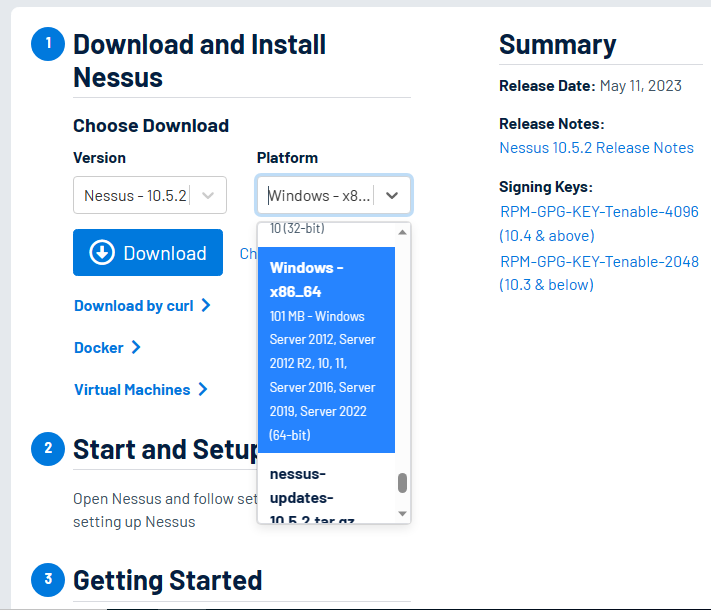
The version and platform selected can be seen below. Click download and accept licenses.
Once finished downloading, open the wizard and click next. Accept the license agreements and click next.
You can leave the destination folder to the default location, click next and install. On the user account control pop-up window, click yes. Then just wait for the installation to finish. Once done, click “Finish” to click the wizard.
A webpage will appear. Click “Connect via SSL”, Advanced, and continue to localhost.
if the below window appears, just click continue.
Once at the page shown below, click on Nessus Essentials and continue.

Click skip and put in the activation code that was sent to your email.
Create a user account with a username and password that can be easily rememberable for this lab.
Then just wait for Nessus to initialize.

Once done initializing, you will be taken to a Nessus Essentials site showing your scans.
I recommend you make a quick note of the URL as you will have to come back to it later on after some restarts.
You may have to wait for the plugins to finish compiling to continue.
While it’s compiling, we can collect the IP addresses of the systems we are going to scan. Simply open the terminal and type ipconfig.
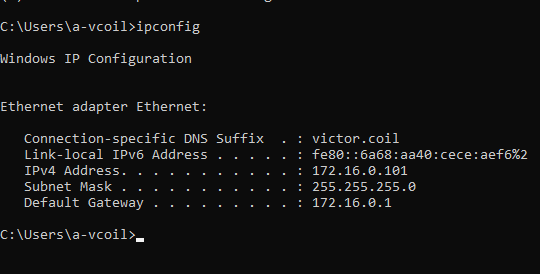
As seen above, the IP of the Windows 10 client is 172.16.0.101, and the IP address of the Domain Controller is 172.16.0.1.
Non-Credentialed Scan
Performing a non-credentialed Scan
Once everything is done compiling, click on “New Scan”. You may have to scroll to the right a bit to see the button.
Then click on “Basic Network Scan” as seen below.
The first scan will be a non-credentialed basic scan. The image below is the name I placed for the scan and the target IP which is the Windows 10 Client IP.
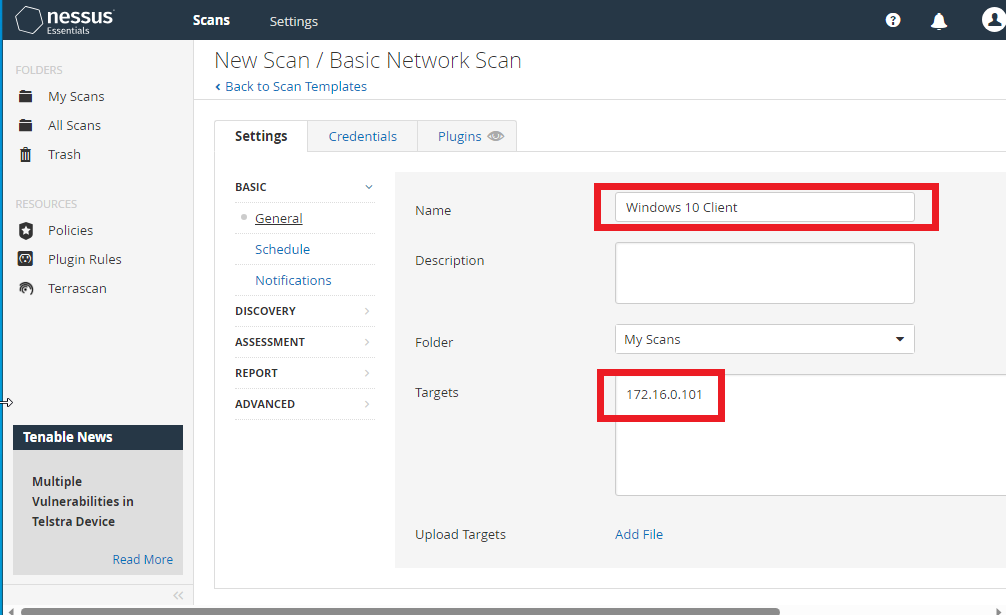
After making those two changes, just click save at the very bottom. We will be sent back to the “My Scans” page and a new scan will be there as shown below.
To start the scan, simply click on the arrow at the right side of the scan.
The green symbol shown below will let you know that the scan is currently being ran.
Once finished, the green symbol will be replaced with a checkmark.
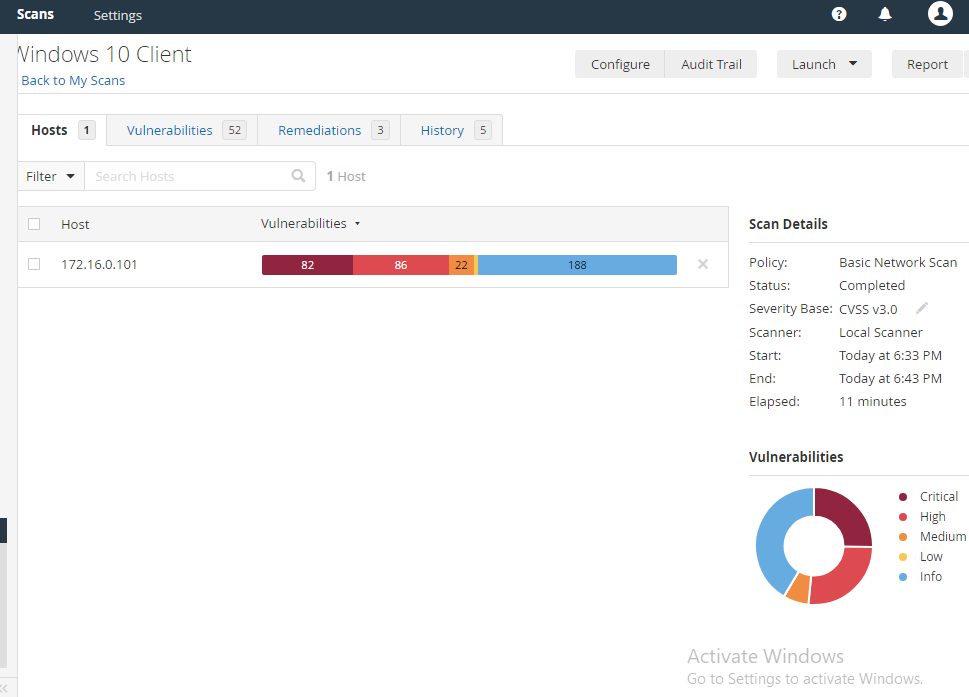
Once you see the checkmark, click on the scan to see the results. Below are my results for the windows 10 non-credentialed scan.
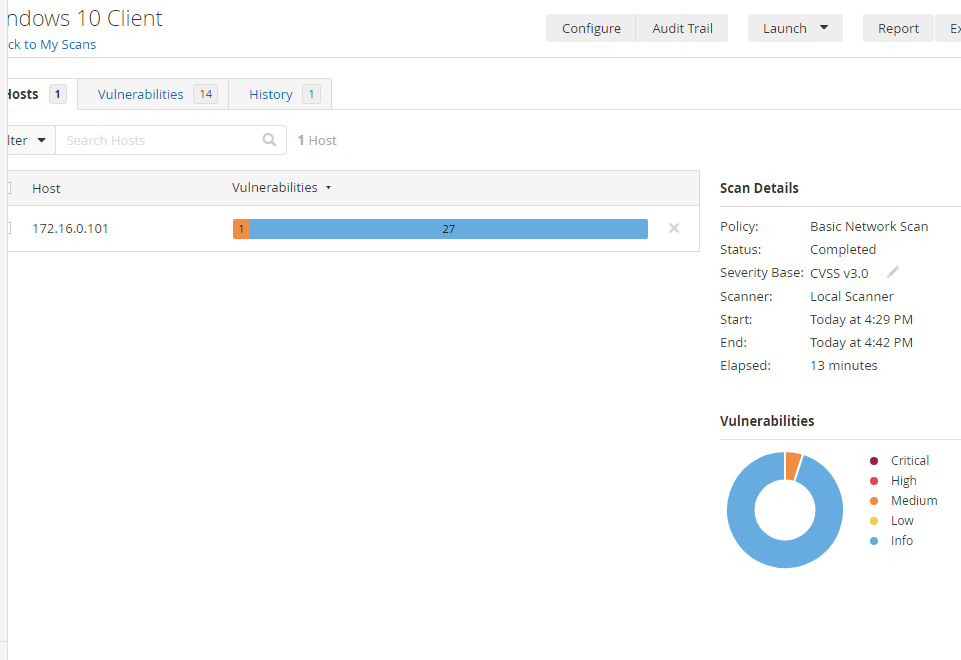
At the very top, you can click on the vulnerabilities tab and go through them. Vulnerabilities tagged with “Info” usually just wants you to be aware of them. If you can click on the medium vulnerability, it will also give you some solutions that can be used to mitigate/patch the vulnerability.
Credentialed Scan
Performing a Credentialed SCan
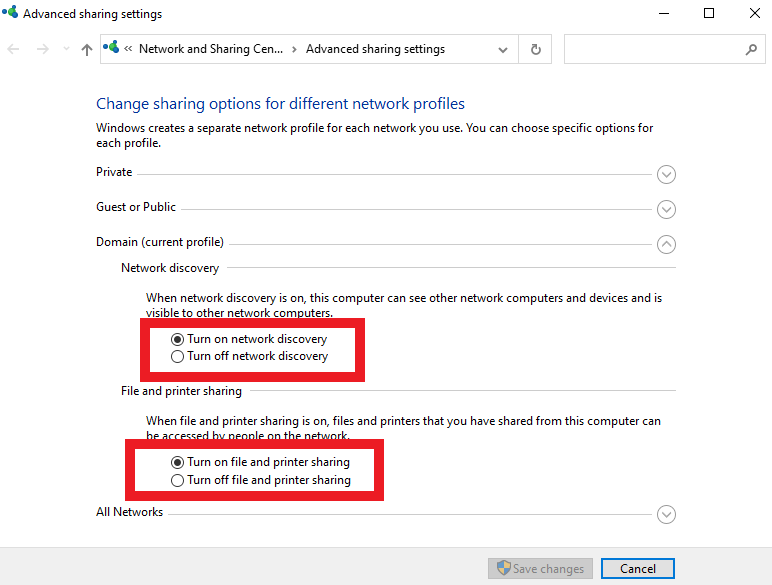
Now for a Credentialed scan. This will allow the scan to go deeper and find more vulnerabilities. Before diving in, we need to make sure that network discovery and file/printer sharing is on.
On the Windows 10 Client, go to the search bar and type in “share”. Click on the option shown below.
Make sure that the two options shown below are turned on.
After those changes. Let’s now perform a credentialed scan.
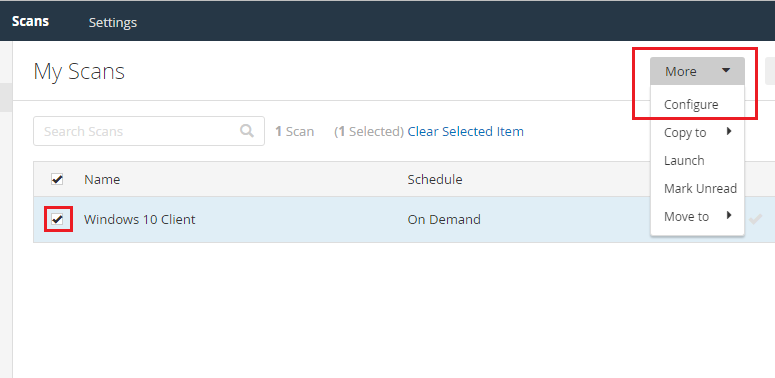
On the top left, click on “My scans”. Once back at the “My Scans” page, click on the checknox to the left of the scan name, then a new box will appear at the top. Click on more, then configure.
Then click on Credentials at the top, then “Windows” as shown below. Fill in the Username and Password with the account you are using on the Windows 10 Client.
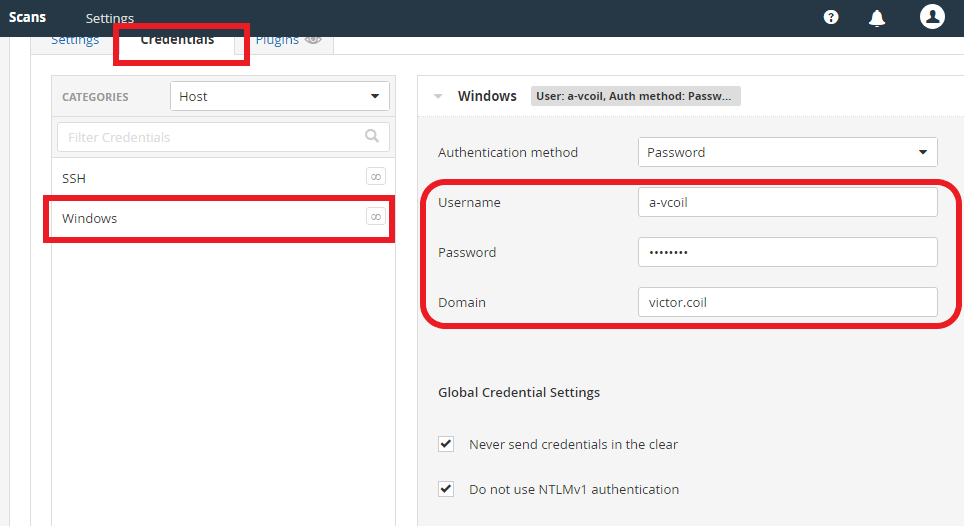
After adding these credentials. Click save at the bottom and go back to the “My Scans” Page. Then run the scan one more time.
Because this is a credentialed scan, we will see more vulnerabilities. Once this scan finished for me, there were 4 Critical vulnerabilities and 15 High Vulnerabilities. These vulnerabilities were mostly just Edge and other Windows Native Applications that just needed to be updated.
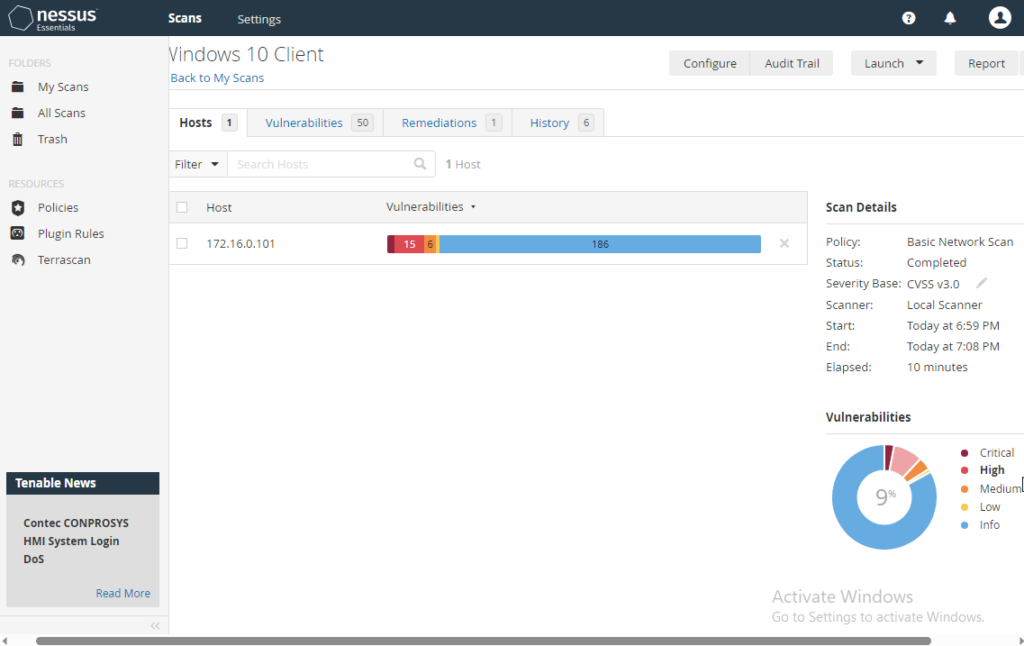
Credentialed Scan with Deprecated Browser
performing Credentialed Scan with deprecated Firefox
Let us explore and see what a single deprecated app on our systems can do.
The deprecated app that I will use is Firefox. Simply google “Download old Firefox”, and click on the first link which is shown below.
Inside that link, scroll down until you see the section shown below, and click on the link with the red box around it.
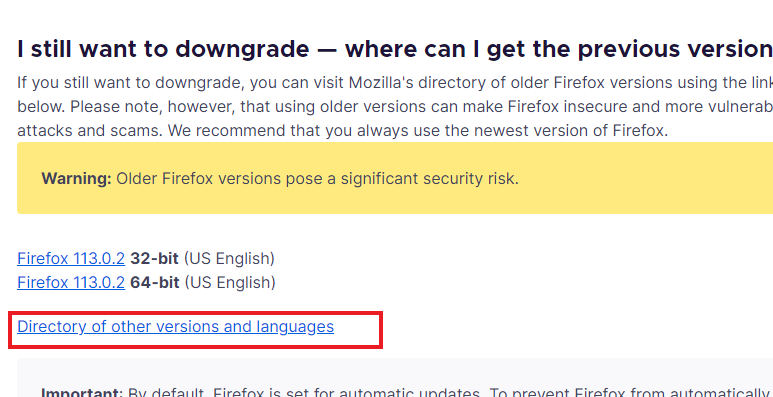
Then scroll down until you see 3.6.12
Then click on “Win32”
Then click on “en-US/”
Then select the top .exe file. Once downloaded, in the wizard just keep all defaults and standards and keep clicking on next then install.
Once Firefox is done downloading and installed. Go back to Nessus and restart the credentialed scan.
Once the scan is finished, we can see that many more critical and high vulnerabilities are now present.
From 4 Critical, 15 High, 6 Medium, and 1-2 Low. To 82 Critical, 86 High, 22 Mediums, and a handful of lows. All of this is from just Firefox.
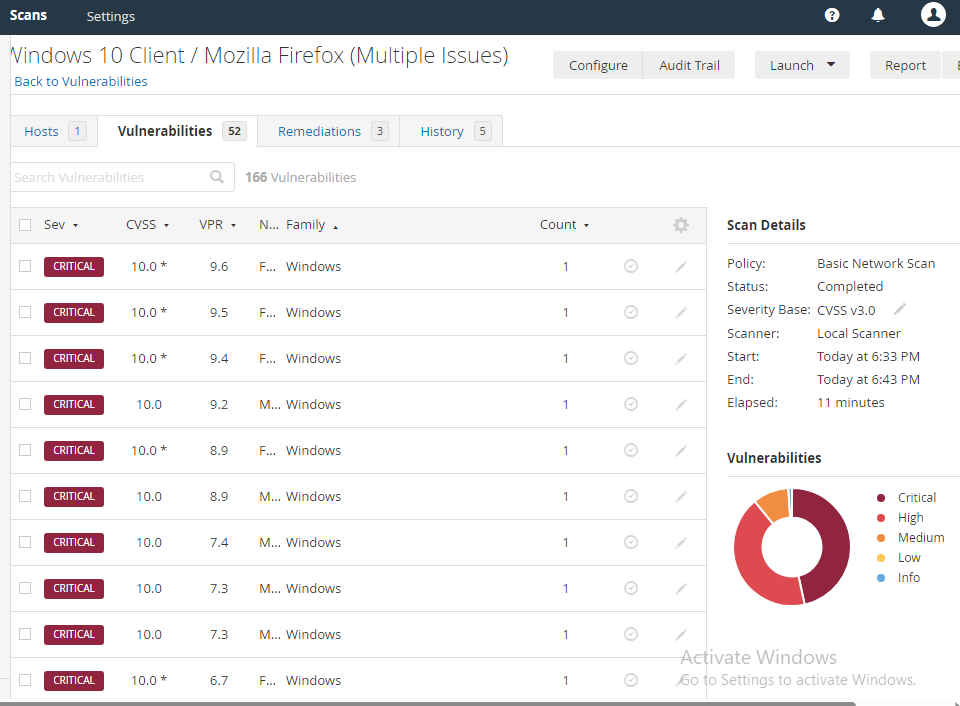
The remediation section tells us that we can upgrade to remediate the vulnerabilities. But we can also just delete Firefox. We can usually approach many applications this way. If you don’t use it, get rid of it. This helps make the attack surface smaller.
Sometimes, there will be situations where you can’t just get rid of it and will have to research on available patching to remediate the vulnerability. Even worse, there are times when you can’t even patch as it can get in the way of business operations. The call will have to be made to just accept the risk.
Remediations
Remediating the Vulnerabilities
Let us do the obvious here and delete the deprecated Firefox. This will get rid of the majority of vulnerabilities.
In the Windows 10 Search Bar, search for “appwiz.cpl”
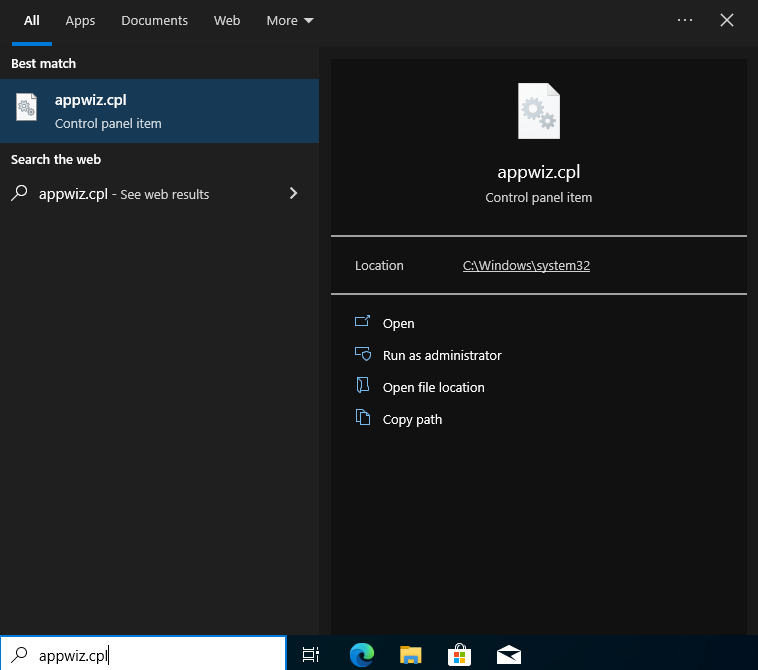
This will open the control panel, programs, and features. Just right-click on Firefox and uninstall.
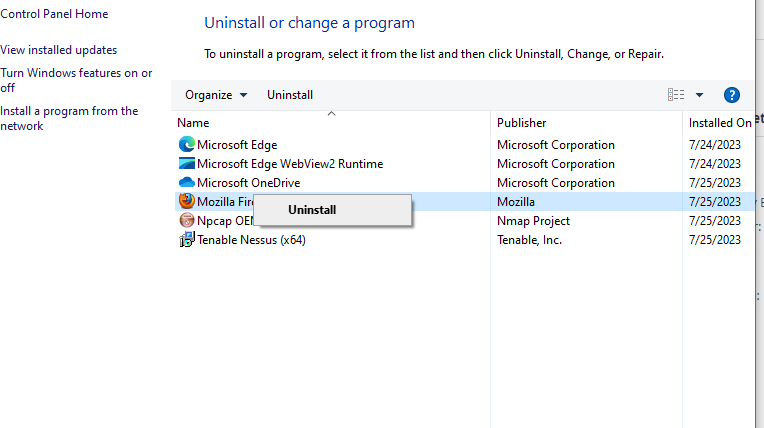
In the wizard just click on uninstall and next.
After getting rid of that, let’s run a Windows update. You can do this by clicking on the start button to the bottom left of the screen, clicking on settings/the little widget, then “Update & Security”.
As seen below, there are a handful of things to update. Just click on Install now. Once finished, click restart PC.
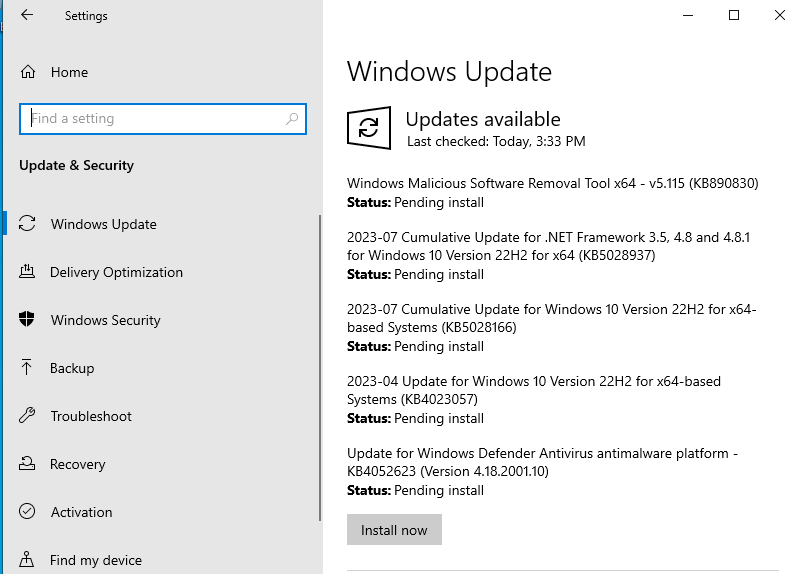
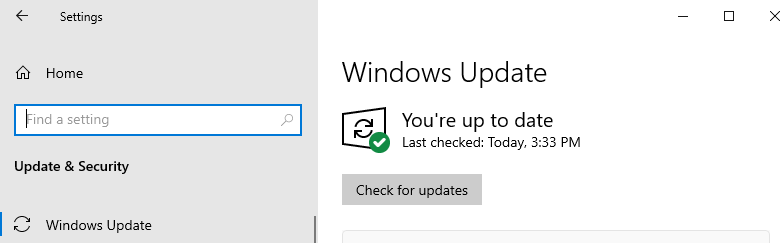
After resetting and seeing that there is nothing else (Make sure you click on “Check for updates”. You may have to do it a couple of times.)
After that, Open up the Microsoft Store. There will also be updates available for apps here.
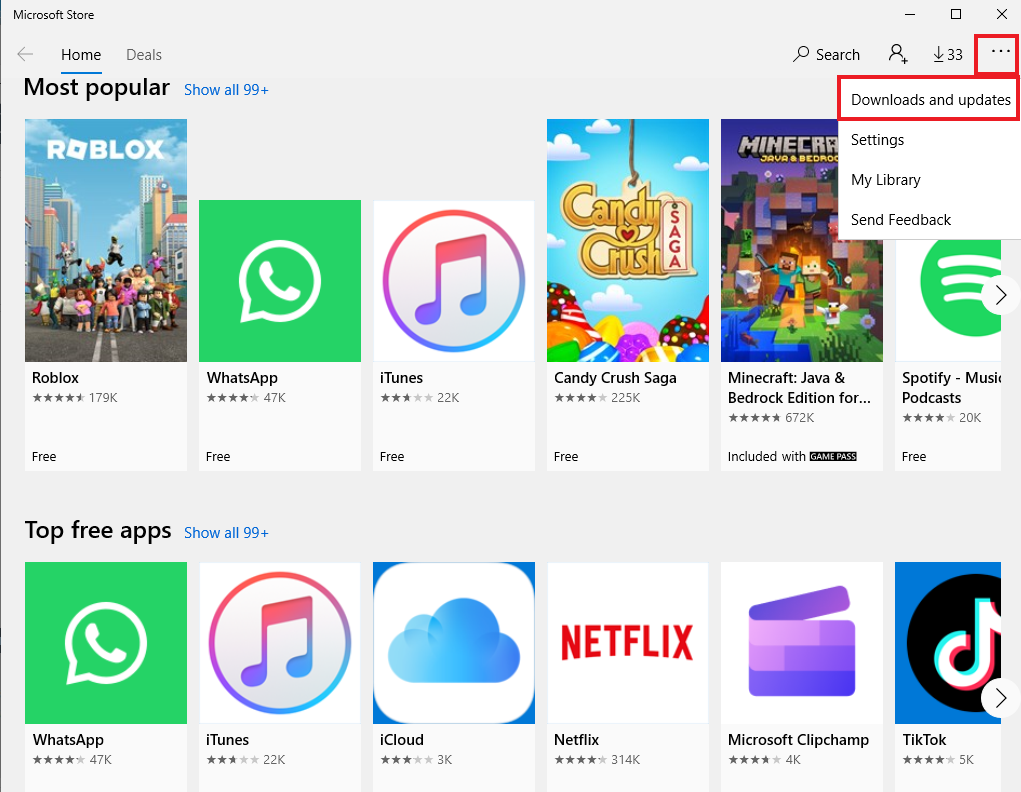
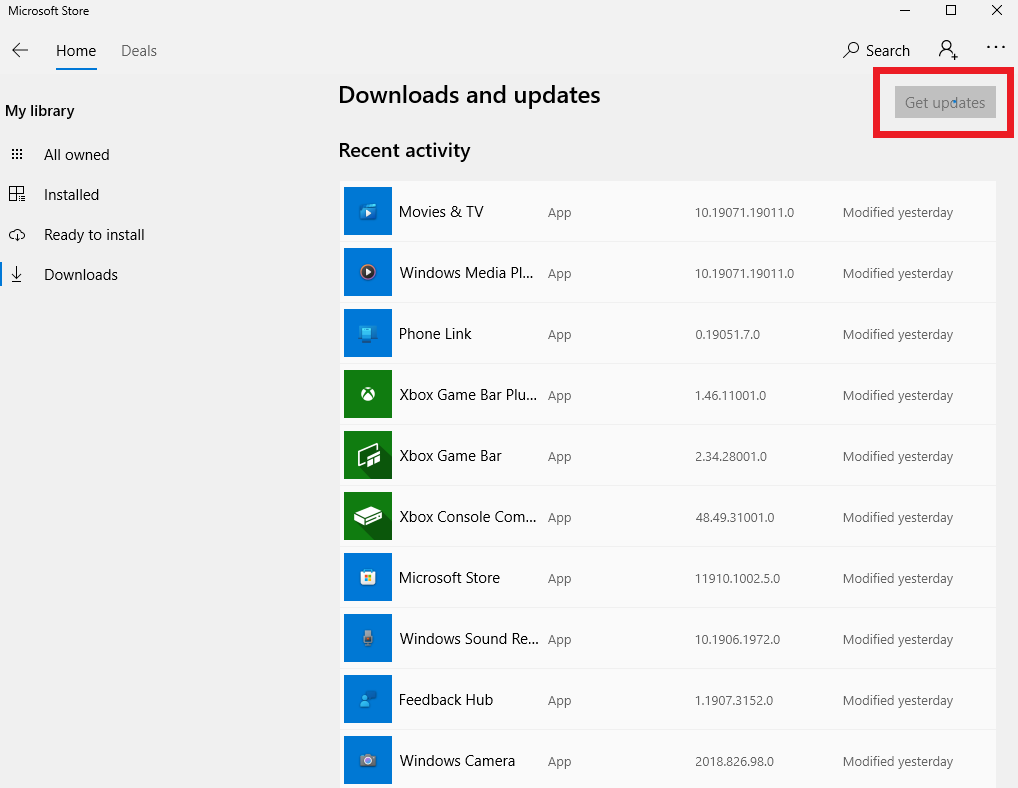
The whole layout of the store may change after updating a bit. The second layout, this is where I was able to find the updates.
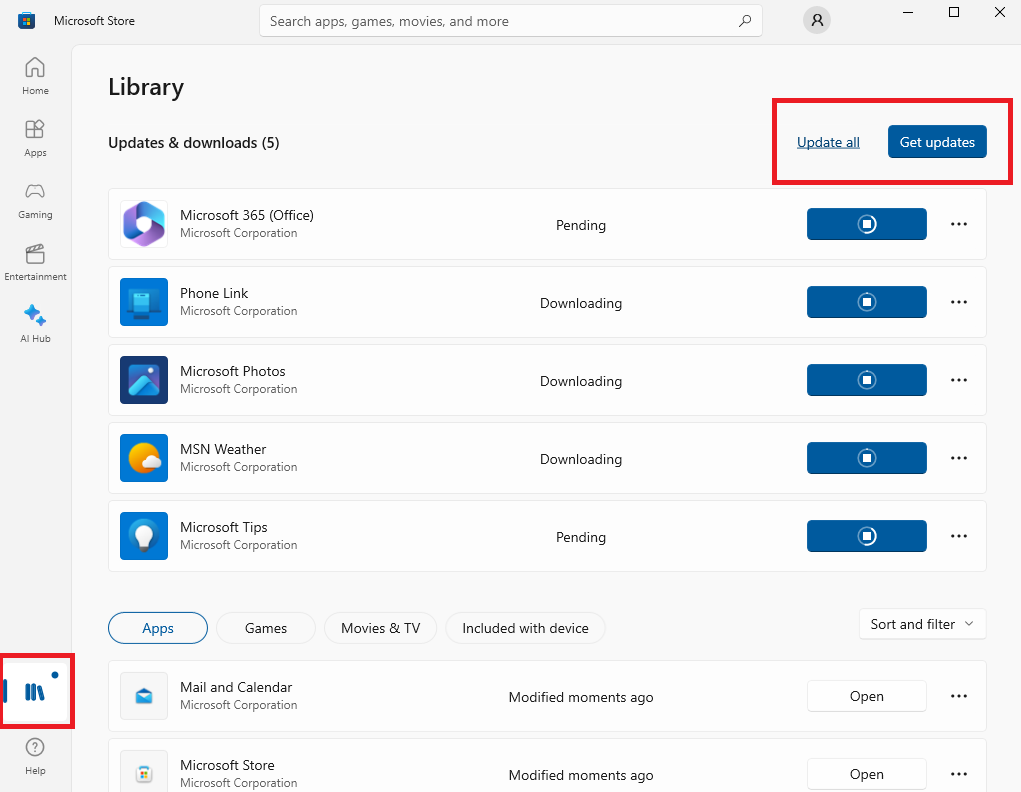
After performing these updates, rescan the system.
As seen below, the critical and Highs have dropped dramatically.
With there being 1 Critical, 1 high and 2 mediums, and 181 info.
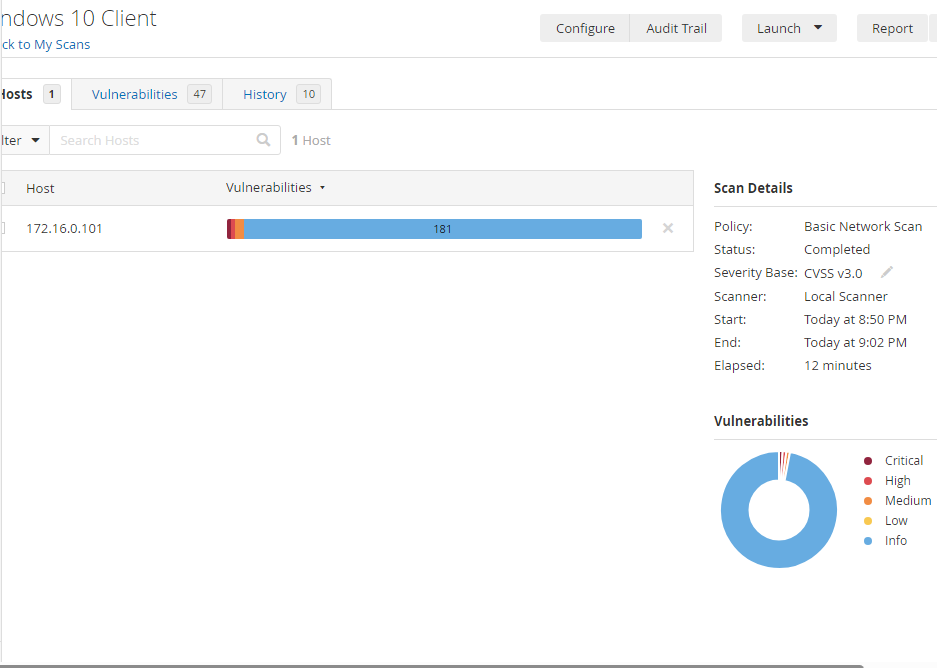
The critical Shown Above is that Internet Explorer isn’t turned off and that some functionalities present in it can be used against us. We have to disable and create a specific registry key. Let’s continue remediating.
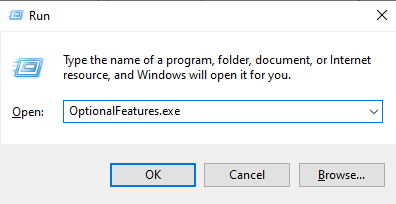
I clicked on the Windows key and R key at the same time. In the little pop-up window, I searched for the executable shown below.
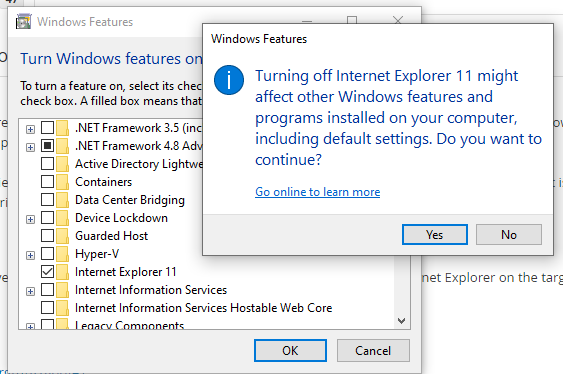
Then unchecked Internet Explorer 11 and clicked Yes. After this, you will have to do a quick restart.
Now for registry keys. Click on the Windows Key and R key, then search for “Regedit”.
Navigate to “HKEY_LOCAL_MACHIENS\SOFTWARE\Policies\Microsoft\Policies\Microsoft”.
Right Click on Microsoft and create a new key. Name this new key “Internet Explorer”.
Then make a subkey by right clicking on “Internet Explorer” and clicking on “Key”. Name the new key “Main”. Then right-click “Main” and make a DWORD (32-bit). Name this one “NotifyDisableIEOptions”. Right-click on the newly created DWORD, and click “Modify”. Set the value data to 1.
These changes will handle the Critical Vulnerability.
Nessus tells us that the High is us being vulnerable to CVE 2013-3900. Their solution requires us to add “\wintrust\config\EnableCertPaddingCheck”.
Inside of Regedit, Move over to “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Crytography”
Right-click on Cryptography. Hover over New then click on “Key”. Name the first key as “Wintrust”. Then Right Click on Wintrust and create another key. Name this subkey “Config”.
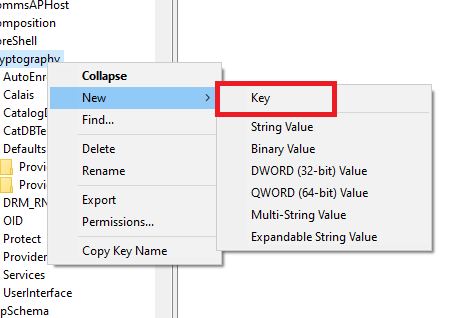
Right Click on “config” and instead of making a new key, click on “DWORD (32-bit)”. Name this “EnableCertPaddingCheck”. Once made, double-click it and as shown below, put 1 in the value data field.
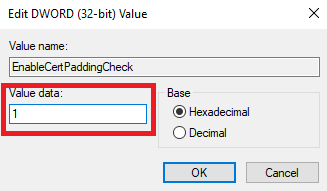
Then move over to “HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography”. Right Click on Cryptography and create a new Key with the Name “Wintrust” and then another subkey with the name Config. Then right-click on Config and do a DWORD (32-bit), name it EnableCertPaddingCheck. Then right-click on it and set the value to 1.
After performing these changes and running one more scan, there were only 2 medium vulnerabilities left with 185 Info.
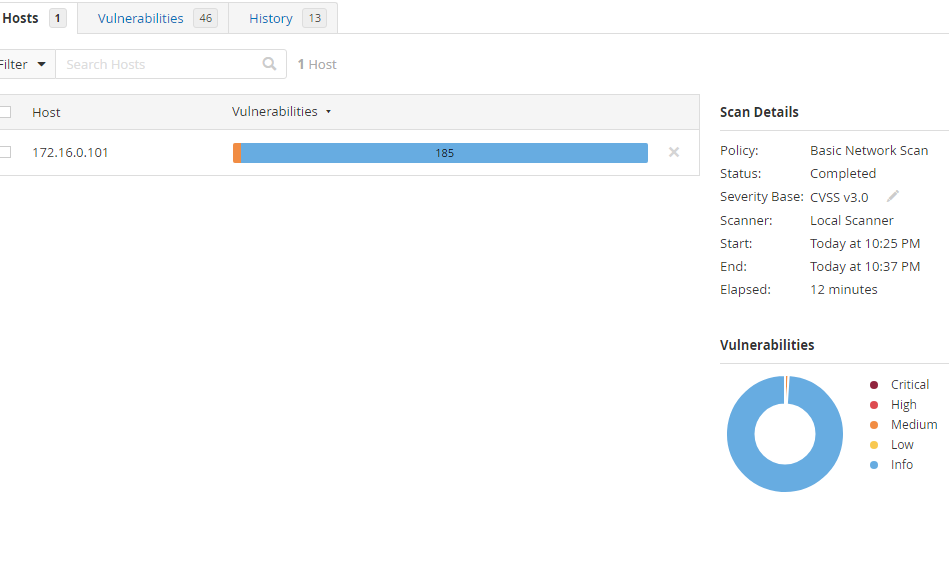
We can simply accept the leftover vulnerabilities. We successfully removed all critical, high, and a handful of medium and low vulnerabilities.
This concludes the Vulnerability Management Lab.
