Splunk Deployment
Deploying Splunk Enterprise
Prerequisite Labs
Lab Brief Summary
This lab will cover the deployment of Splunk Enterprise and Universal Forwarders onto an Active Directory Environment for Centralized Logging. Enhanced logging will be done using Sysmon. As well as the deployment, Configuration, and integration of the IDS tool Snort into Splunk.
Splunk Free Trial Download
To get started, we need to get the downloads for Splunk Enterprise and the Universal Forwarder.
We can open our browser inside Client1, search for just “Splunk” or copy the download link above and paste it into your VM, and then click Downloads.
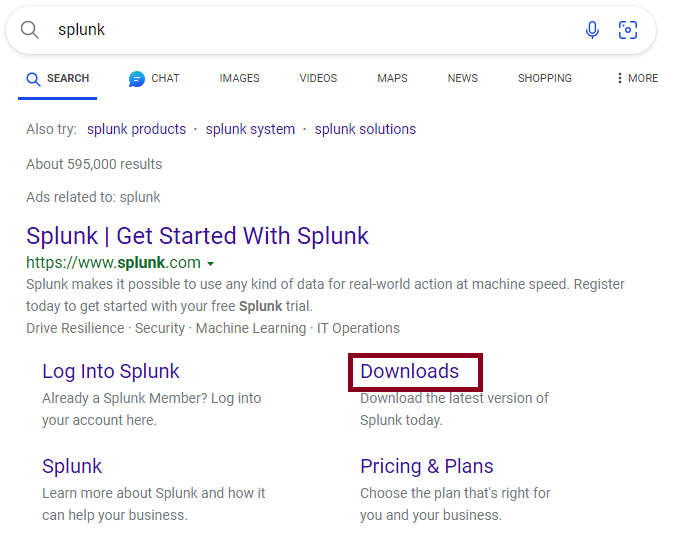
We will be deploying Splunk enterprise on Client1. Client1 will be where out logs will be centralized. Click on “get My Free Trial”.

After clicking the button, fill in the information and click on the button to create an account and move on.
Then for this case, we’re using Windows 10 so just click on Download Now on the 64-bit Windows version.
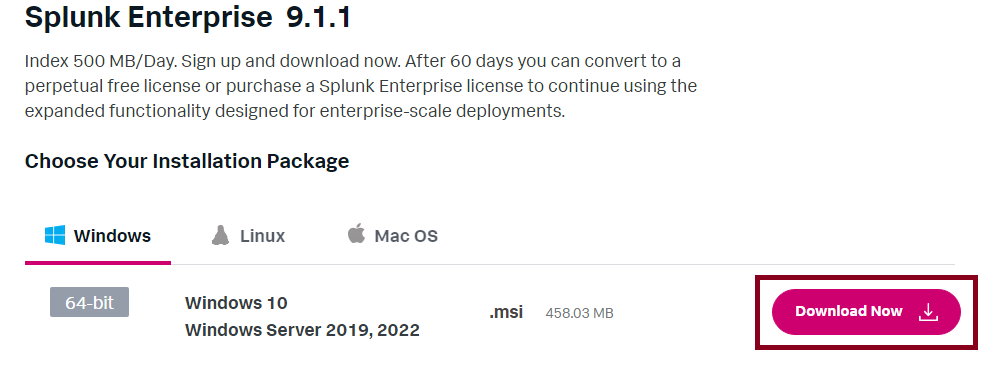
Once downloaded, the installer will open up automatically. The Browser window might get in the way so keep an eye on the task bar.
Accept the License Agreement on the installer box and click next.
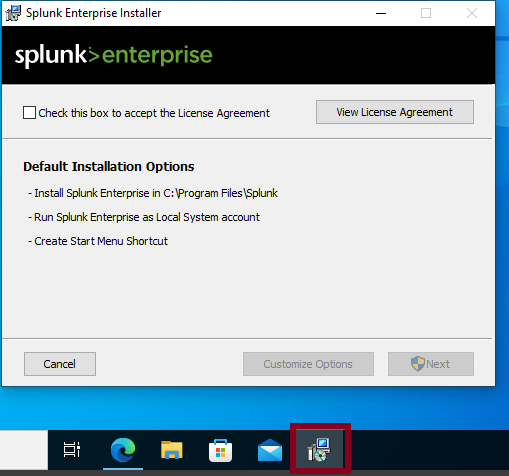
After Hitting next, you’ll be asked to create some credentials for the Splunk administrator account. For this lab, I’ll be using credentials that are easily rememberable.
After that, click next then click install.
If the User Account Control panel pops up, enter a Domain Administrator’s credentials in to allow changes.
After giving it some time, Splunk Enterprise should be successfully installed. Click on “finish” on the Setup window.
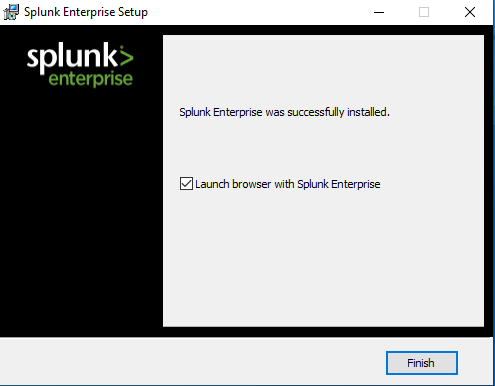
You can access the Splunk Web interface using
Or
Then you’ll be greeted with the login in page. Use the credentials you created during the setup.
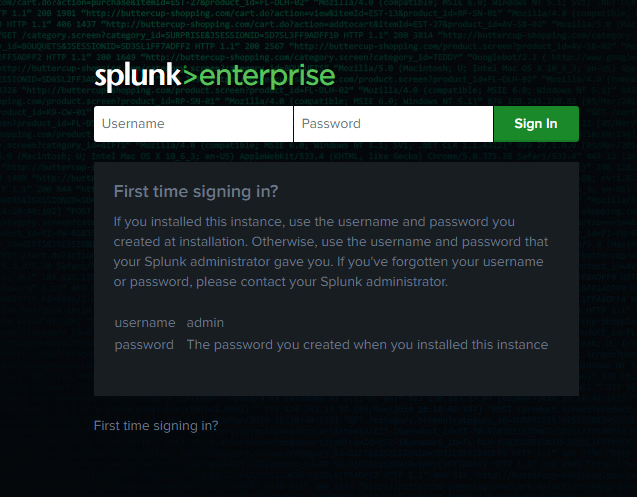
Once logged in you’ll be greeted with the Splunk Dashboard. Navigate to Settings at the top of the page. Then click on “Forwarding and receiving”.
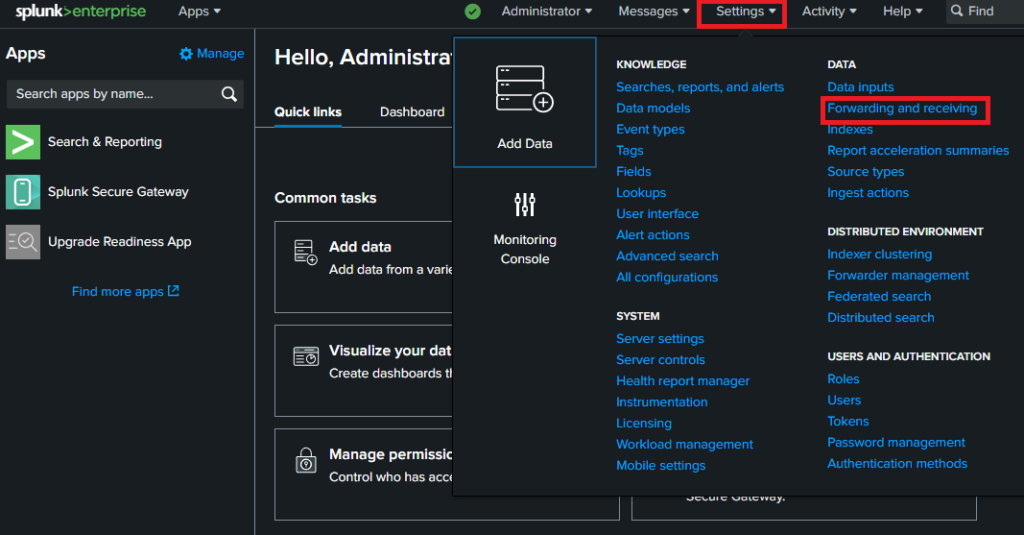
Then click on “Configure receiving” as shown below.
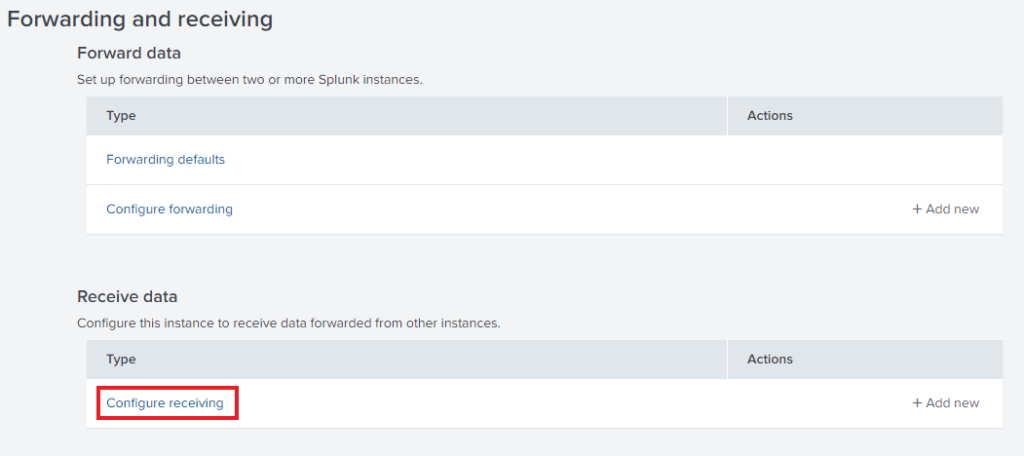
Click on the Green button on the top right that says “New Receiving Port”.
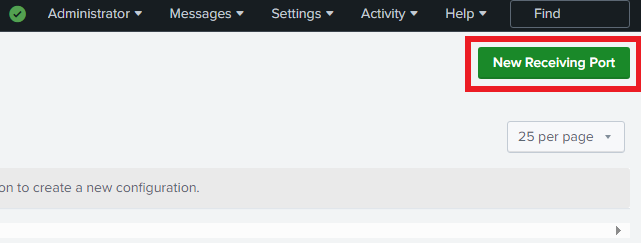
Plug in 9997. This is the default receiving port. Click save after.
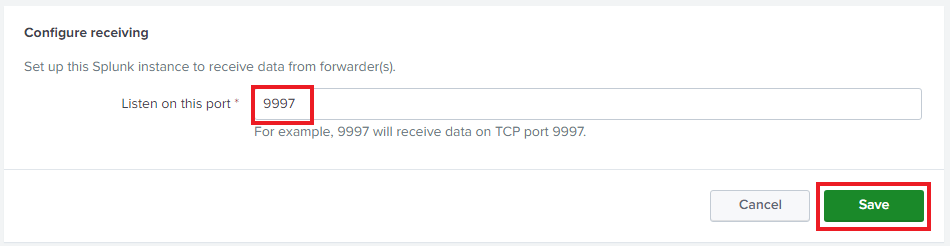
Once you click save you will see the same as below.
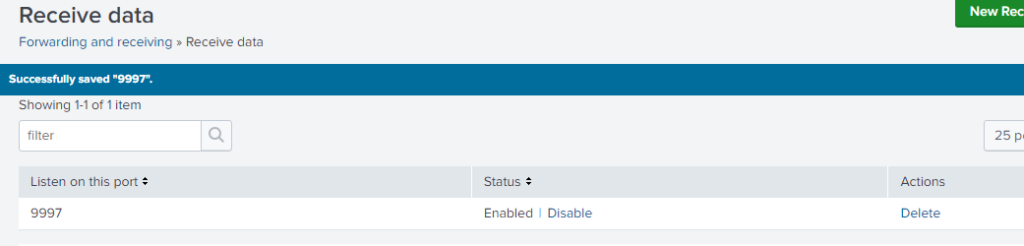
After that, the Client1 Machine is set up. We can now switch over to the domain controller and deploy the Universal Forwarder.
Open up a browser and search up “splunk” just like last time. But this time click the button under the Universal Forwarder.
You wont have to put your information again, just click on log in.
You may have to verify your email address, but after that try again and it should let you into the downloads page.
For the Domain Controller, click on the Windows 64-bit Download button.
Accept the Agreements at the bottom of the next page. Then Open the file once done downloading, The Forwarder setup window will appear.
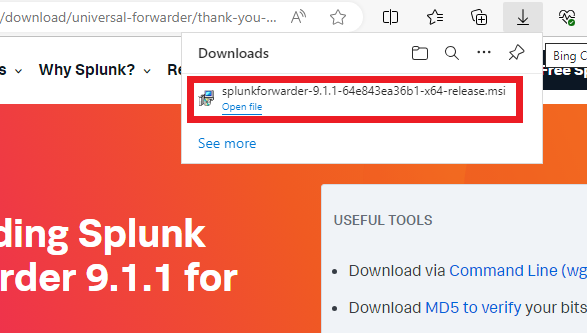
Check the box to accept the License Agreement, then click on the “Customize Option” Button.
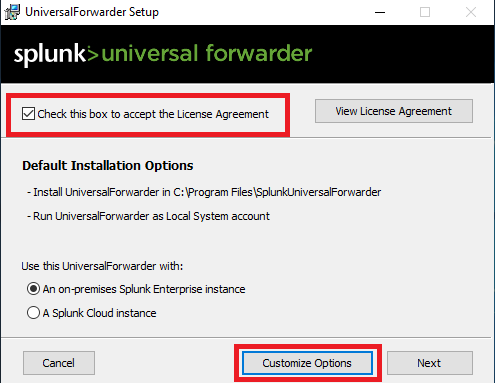
Keep the default install path and click next.
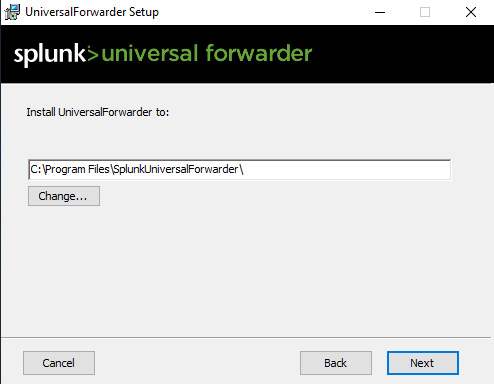
When it comes to the certificate information, leave it default.
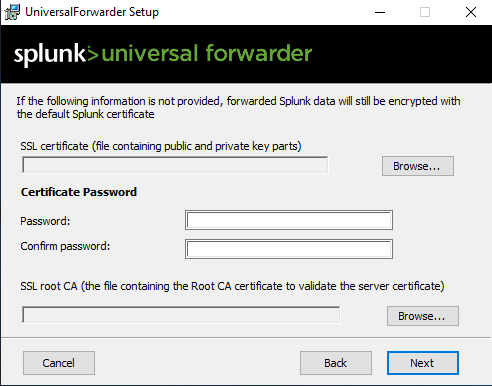
Leave the default local system authentication.
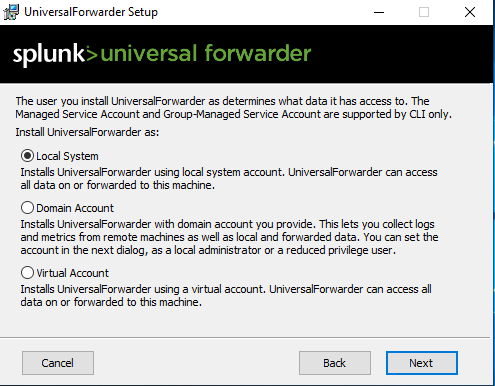
Check every box to monitor everything, click on the “Directory” button, and click on “Local Disk (C:)”. then click on OK.
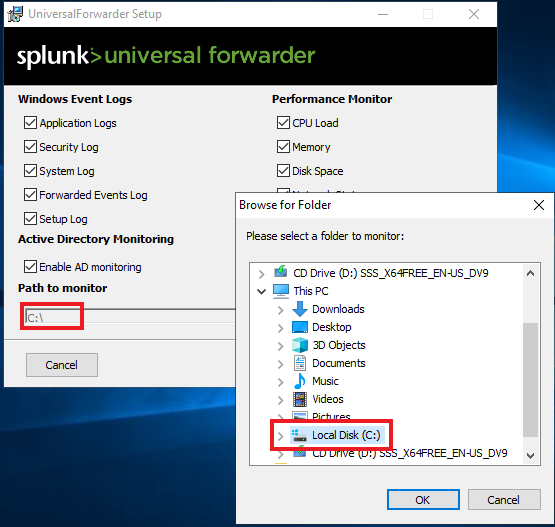
You should see the “Path to monitor” as “C:\”.
Click “Next” once done.
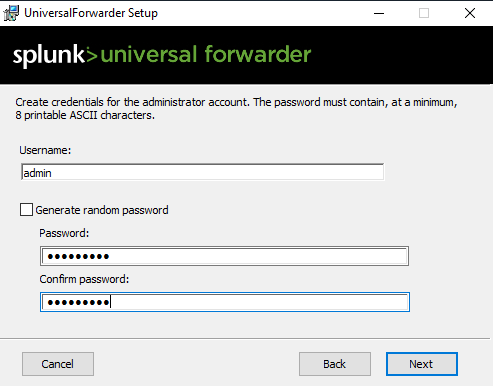
Then create a forwarder account. I used the name admin for this one.
The next window will ask for the IP Address of the Deployment Server. In this case, this is Client1.
The IP address is 172.16.0.100 for Client1, it may be different for you. I will use the default port as shown below.
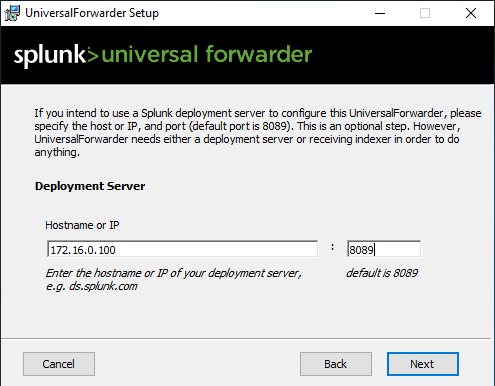
For the next step, plug in Client1’s IP address with the default port of 9997 and click next.
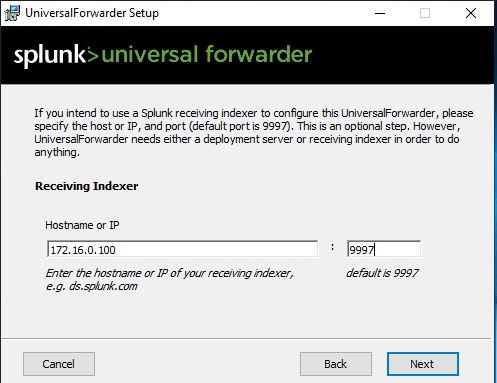
Then click install. Once finished you’ll see the window shown below. Then you can just click finish.
You must make firewall rules to allow the DC to send data to the Windows 10. Search for “fire” and click on the first option.
Then click on advanced settings.
Make sure you are in the inbound rules, and on the right side click on new rule.
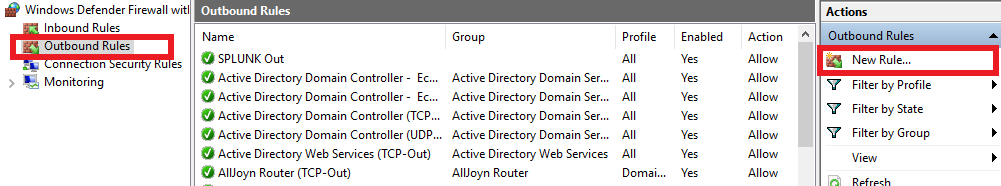
Click on Port, then Next.
Leave as TCP
For the specific ports, put “8089, 9997, 389, 3268”, then click next.
Allow Connection, which should be the default. Click next
Leave Domain, private, and public checkmarked. Click next.
Then name it. I used “SPLUNK OUT”
Do the same thing on Windows 10, but do an inbound rule instead of an outbound rule.
After this, logs will start being sent from the DC to the Windows 10. You may have to restart the Splunk Forwarder on the DC.
Integrating Sysmon
Sysmon for Enhanced Logging
In your browser search for “sysmon github” and click on the first link by swiftonsecurity. Inside of the github, click on the file shown below.
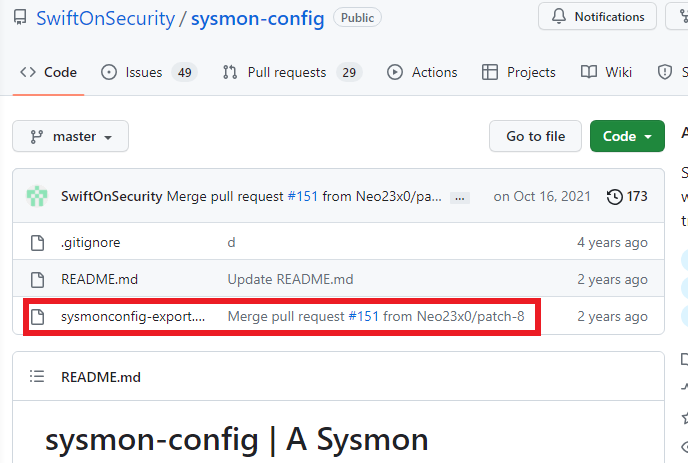
Click on the download button on the right side of the page.
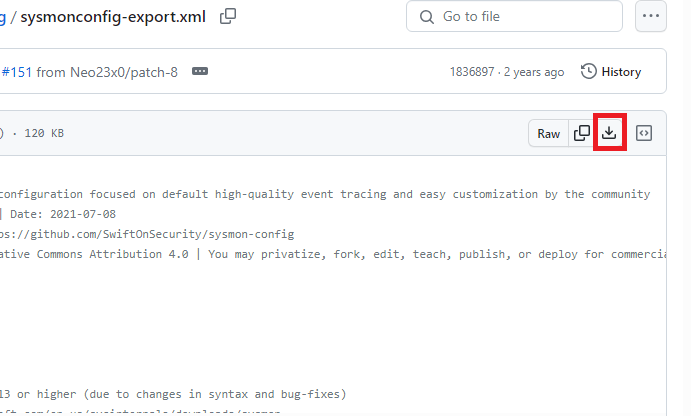
Search for just “Sysmon” and click on the top link.
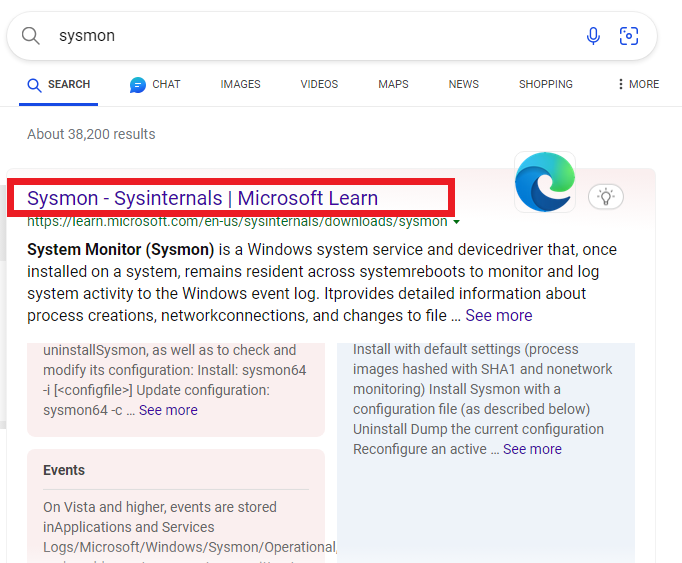
Then click on “Download Sysmon”.
Once downloaded, open up your Download folder and extract the sysmon.zip. Once extracted, move the sysmoncong-export file into the Sysmon folder.
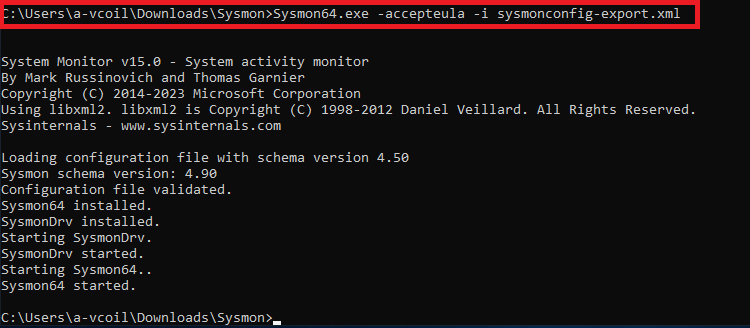
Then open up the terminal as administrator and navigate to the Sysmon folder inside of the download folder and run the command shown below.
If is successful, it will show the same output.
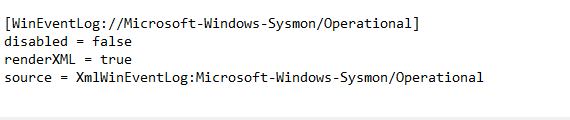
Now open up file explorer at the bottom, and navigate to “C:\program files\splunkuniversalforwarder\etc\apps\splunkuniversalforwarder\local\inputs.conf” and at the very bottom of the configuration file add the code shown below.
Close and save. Now search for services, as we have to restart the Splunk forwarder.
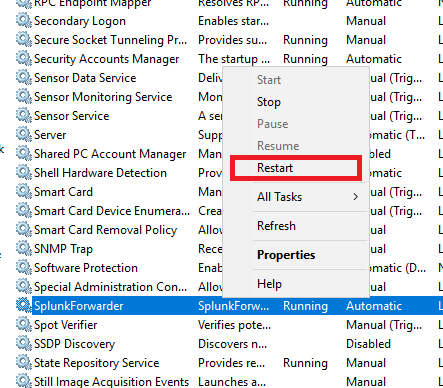
If the service stops after restarting, and doesn’t start back up, just start it back up again. (This happens if you open Services without Administrator Privilege’s)
Back on the Splunk Web site. Click on Apps at the top and click on “Find More Apps”.
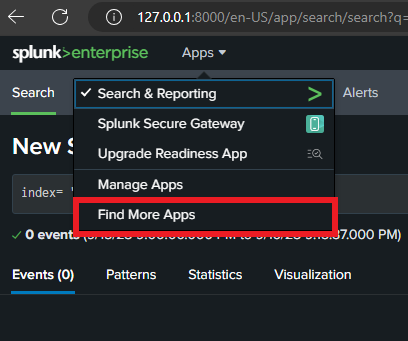
Then search for Sysmon and install the first option.
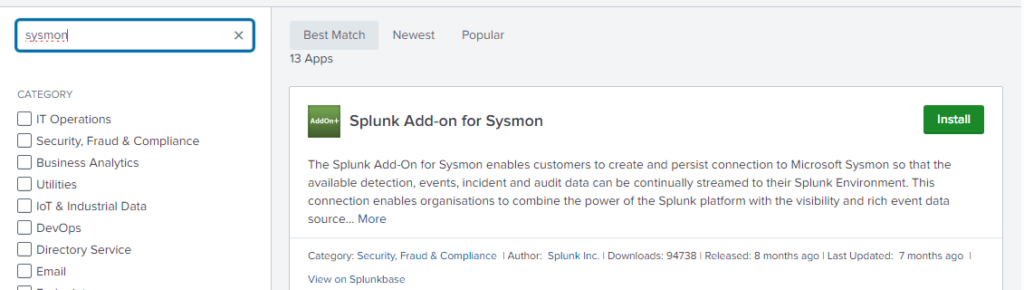
After installation, restart the forwarder.
So after all that.
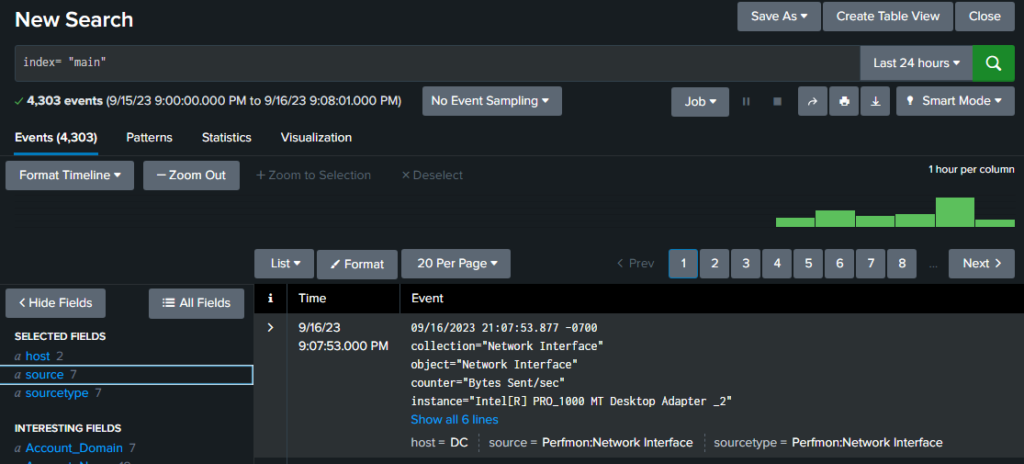
You can go on Windows 10 and test if you’re receiving the DC logs using the search query
Index = ‘main“
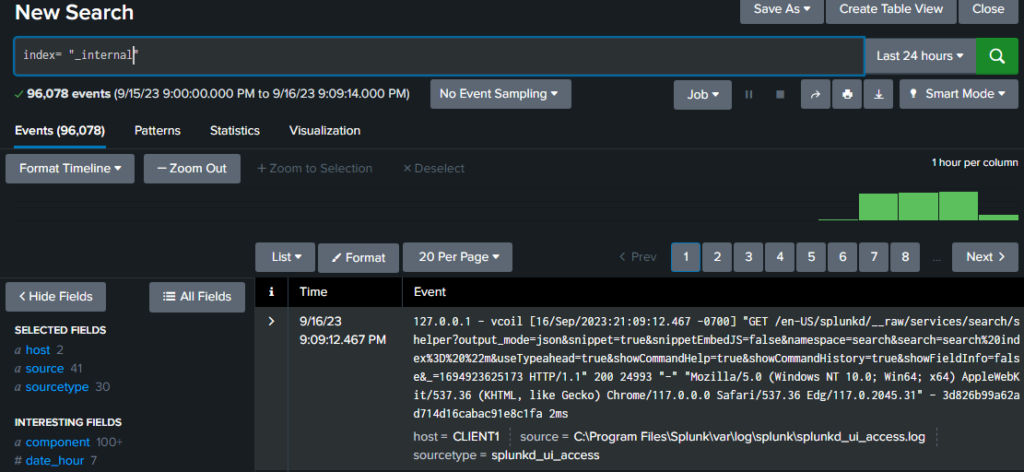
If you’re interested in the Windows 10 logs, you can do
Index = _internal
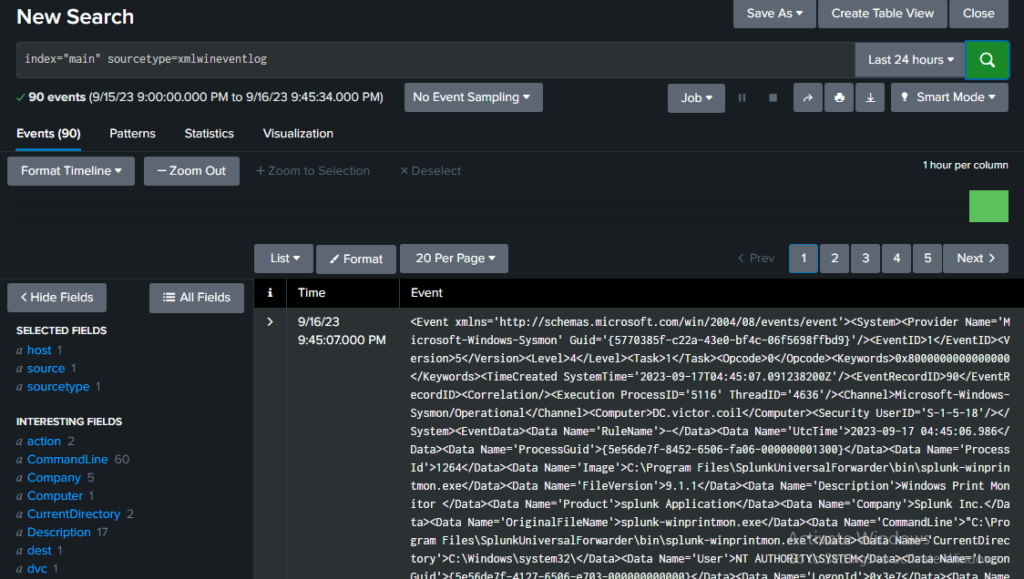
To search for the sysmon logs specifically you can search for
index=”main” sourcetype=xmlwineventlog
Deploying Snort
Integration of the Instrusion Detection System
We will now deploy snort onto the domain controller.
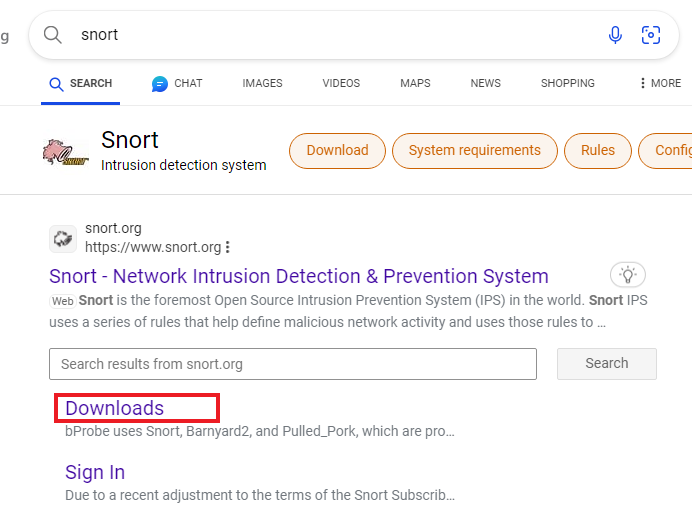
Simply open up a browser inside of the DC and search for snort. Then click on downloads as seen below.
Once there, scroll down to the snort 2 section and click on the .exe file to download snort.
Open the downloaded exe, and it will open up the setup wizard. Agree to the license agreement.
Leave all three components check marked and click “Next”.
Leave the default path and click “Next”.
Once completed, click “Close”.
We haven’t installed npcap, so we will go and download that next. They give you the URL to go and get it, so lets navigate to that.

Once at the site, click on “Download”.
Then click on the first link as shown below.
Click on the downloaded .exe and then agree to the license agreement once the wizard pops up.
Leave the defaults and click on install. Once installed click on next and finish.
I won’t dive deep into the rules here, but if you want to set up rules.
Go back in the snort download page, there will also be a “Rules” section. Download the V2.9 Community Rules. You’ll need a tool to open the archived files.
There are community rules where you can easily download, and registered where you need an account to download, and a subscription is where you will have to pay for more rules.
I simply searched for 7 zip and downloaded the version shown below.
Open up the archived folder, and place the community.rules file inside of the c:\Snort\Rules folder
Let’s go and manually change the snort config file.
Open up the file explorer, click on “This PC”, then double-click on the Local Disk (C:).
Navigate to Snort→ etc→ snort.
You may have to change the permissions on the file to make changes.
Right-click on the file and click on properties. Then click on the security Tab, and click edit. Make you can click on “Full control” to allow write and modify permissions. Once changed, click apply, click OK and open the file.
Once open, go to lines 45 and 48 and replace “any” with the Network IP that we are defending. As well as anything that is considered “external”. I just did the “!” or NOT operator, so that any IP that is not 172.16.0.1/24 is considered external.
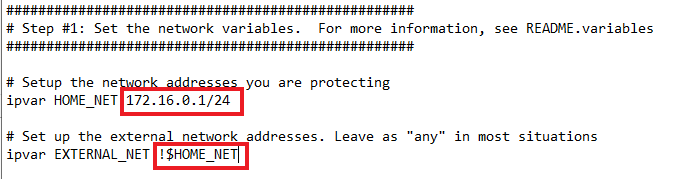
Replace lines 104 and 106 with what’s shown below. Comment out line 105.
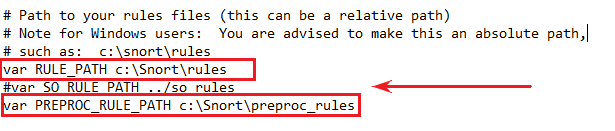
Replace lines 113 and 114 with the below content.
These are the paths to our blacklists and whitelists. For now, we can comment these out. But if you were to bring in the other registered rules, you may need to uncomment these lines.
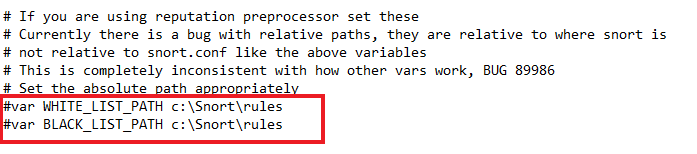
Uncomment Line 186 and place the directory path shown below.
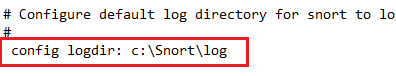
Replace Lines 247 and 250 with the directory paths shown below. Then comment out line 253.
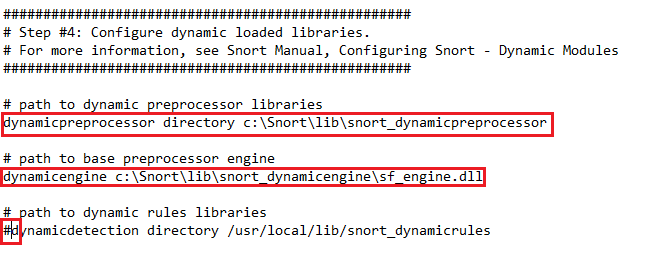
Comment out 265 to 269 as shown below.
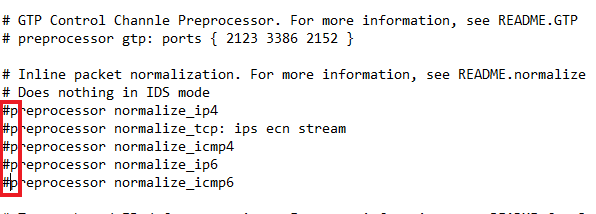
Uncomment line 418 to allow portscan detection. Also, make the additional changes shown below.
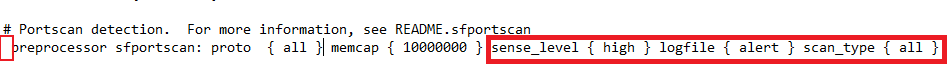
Comment out lines 507 to 512.
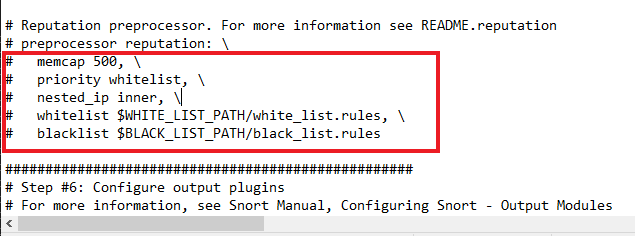
I commented out lines 546 to 651. Future projects will dive deeper into snort rules.
If you do plan on using the other rules, make sure to change the rule paths.
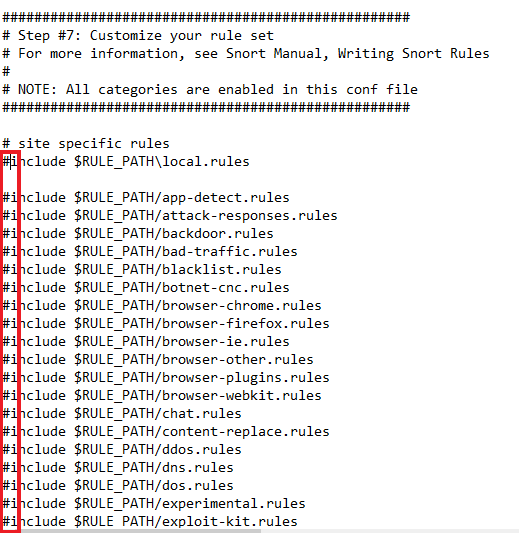
Uncomment 659 to 661 and swap the forward slashes to backward slashes.
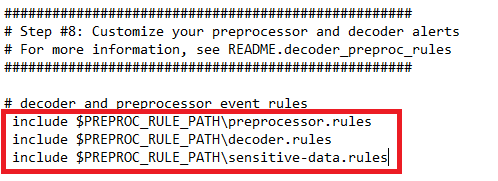
After that save and close the file.
Open up the terminal and cd to “Snort\bin” and run “snort -w”. An error may appear that a vdruntime140.dll isn’t installed. If so, do the following. Otherwise, continue on.
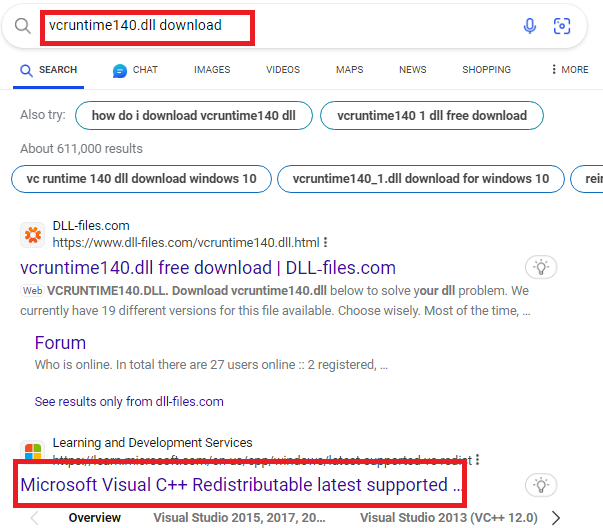
Scroll down until you see the below. Download the X64 version.
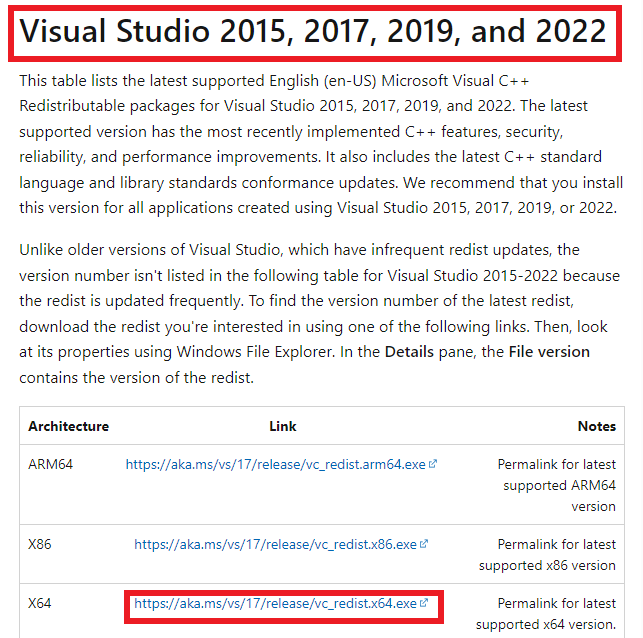
Run the downloaded .exe file.
Agree to the license agreement and click on install. Once done, click close.
Open the terminal and run snort -w again. Take note of the interface with the network we are working with, For me it is interface 5. It may be different for you.
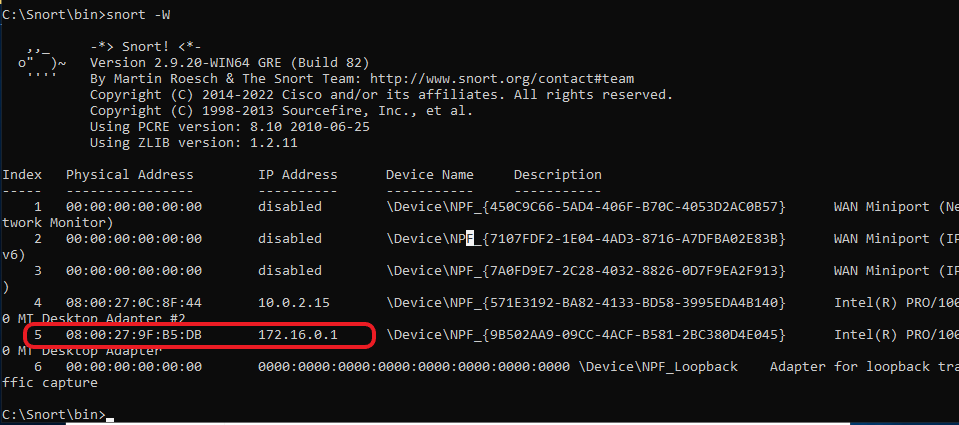
Then run snort -i 5 -c c:\Snort\etc\snort.conf -T
Replace the “5” with the interface that you will be using.
Once ran you will see the content below.
So snorts configuration file is running successfully which is great. Lets just make some small little changes to help logs be readable.
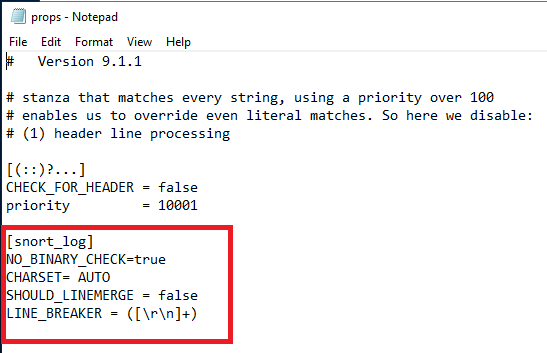
On the DC VM, navigate to Program Files\SDplunkUniversalForwarder\etc\apps\SplunkUniversalForwarder\default\props.conf
In this file, add the content shown below.
Navigate back to Client1 and in the Splunk UI, go to settings, then indexes
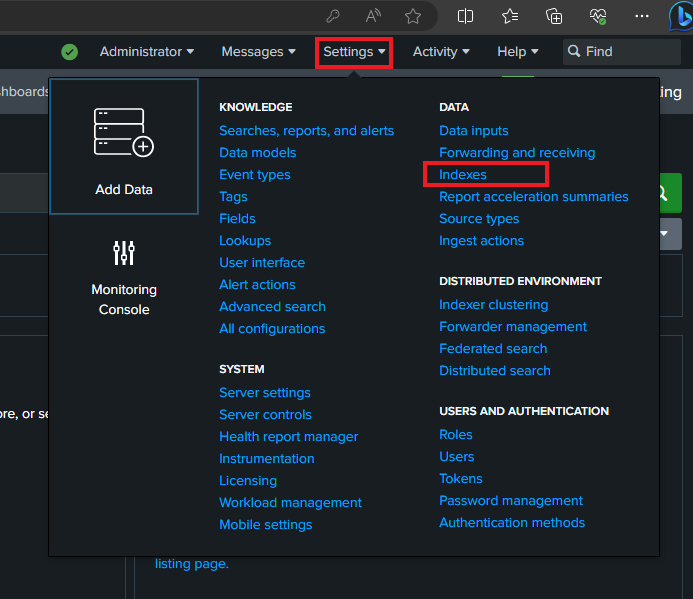
Click on new index
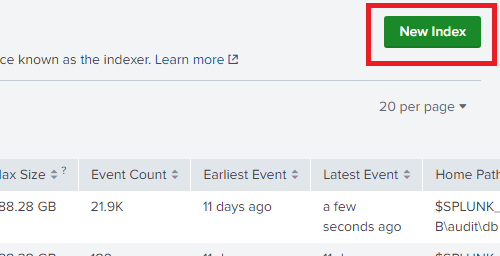
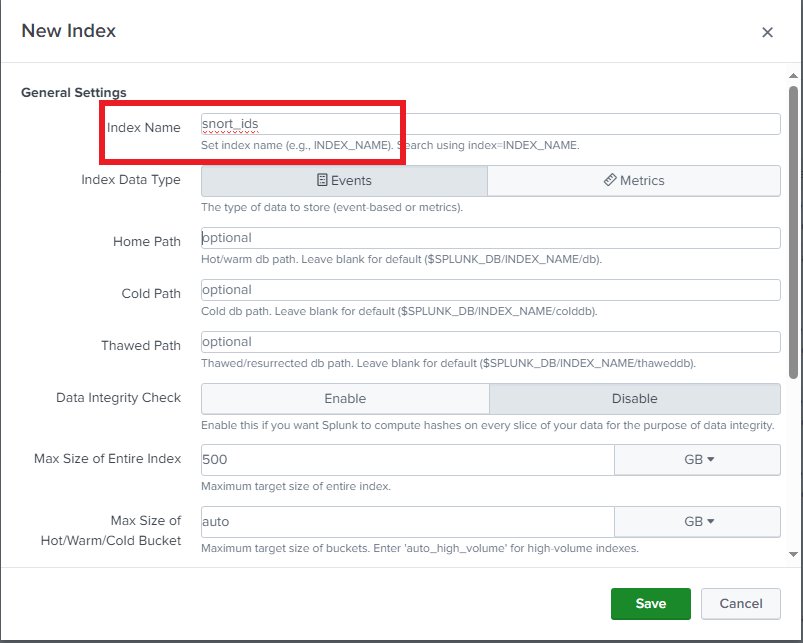
Name it snort_ids then save the index
BACK in the DC, navigate to c:\Program Files\SplunkUniversalForwarder\etc\apps\SplunkUniversalForwarder\Local and open the input.confs file again.
Put the content shown below. Right below the sysmon stuff we added earlier.
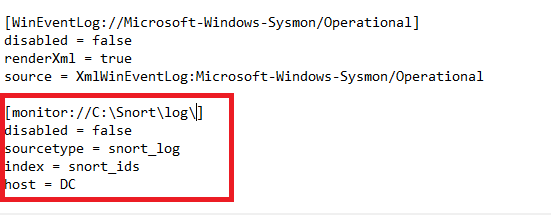
Then restart the SplunkUniversal Forwarder service. You may have to turn it off and then turn it on.
BECAUSE WE COMMENTED a majority of rules out, snort isn’t very noisy. But we still have the rule that can detect port scans. Additional 3-way handshakes may also get picked up by snort.
We should be good to run snort now. Run the command below
Use snort -A console -i 5 -c c:\snort\etc\snort.conf -K ascii
If you want it to run in the background, do this command: snort -D -i 5 -c c:\snort\etc\snort.conf -K ascii
Showcase
Showcasing a bit of Sysmon and SNort
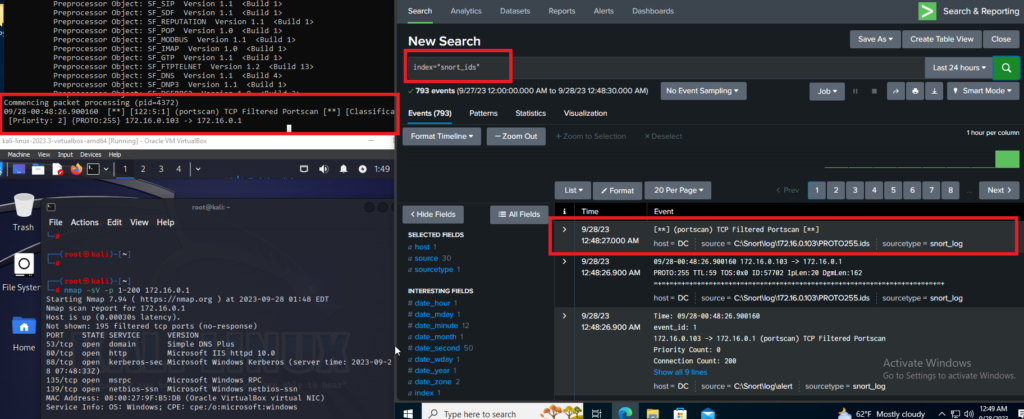
I brought a Kali machine into the environment and performed an NMAP scan.
Bit of a wide picture, but this shows snort running on the DC, and picking up on an NMAP scan. The log is also being pushed into Splunk with the rest of the logs.
So a bit of a showcase on why we integrated Sysmon.
Multiple events by Sysmon can help in detecting threat actors movements. Here are some notable ones
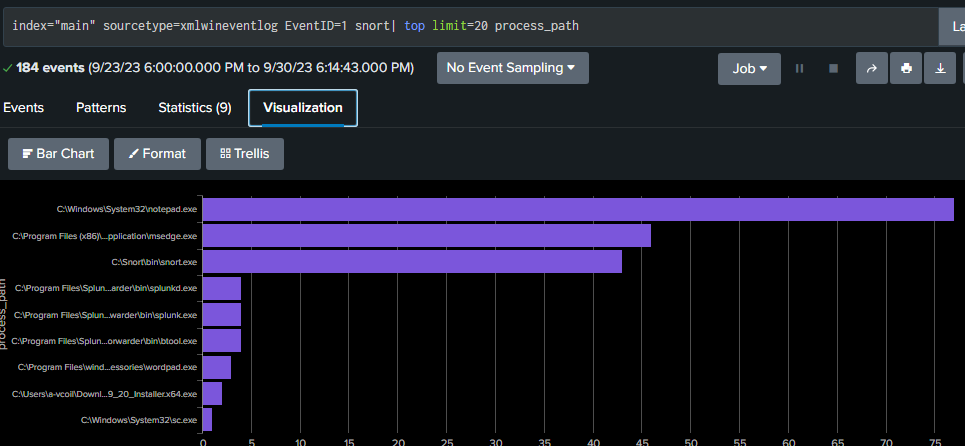
Event ID 1 – Process Creation
The image below shows any process creations that had the word “snort” in it. When doing things like this, it might be better to look at the rare items.
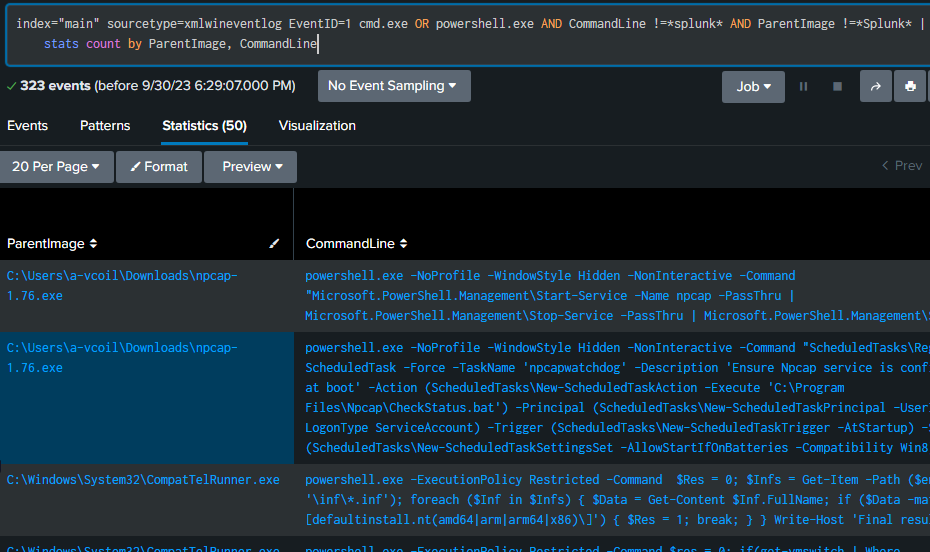
The command below will show if any cmd.exe or PowerShell commands were run.
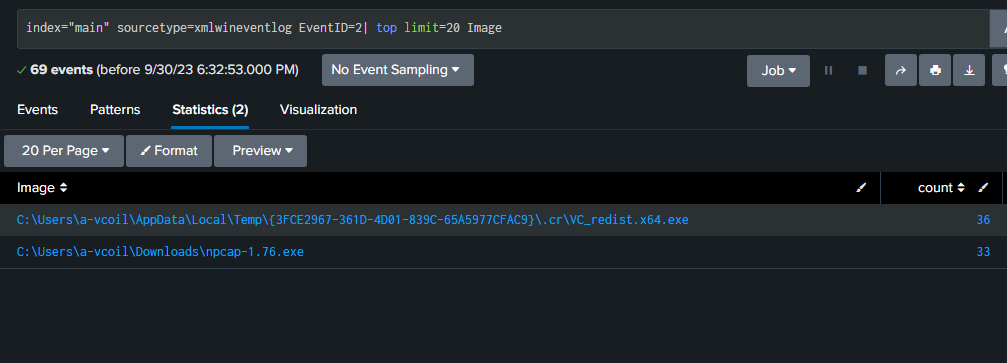
Event ID 2 – Process changed time
The why for this one is if a threat actor is trying to scramble the trail they’re leaving behind. These can help pick up on defense evasion.
Event ID 3 – Network Connection
In this environment, it wasn’t very noisy though it can help in the real world. It can pick up on high network traffic You would have to filter by source IP.
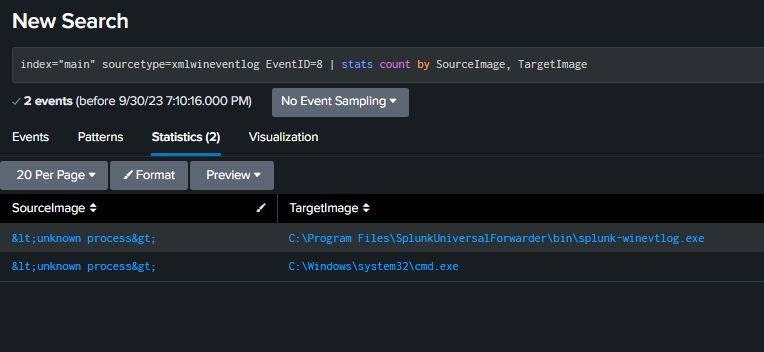
Event ID 8 – Creating Remote Thread
This one is when a process creates a thread under another process.
The below will help pick up on any processes trying to steal from other processes.
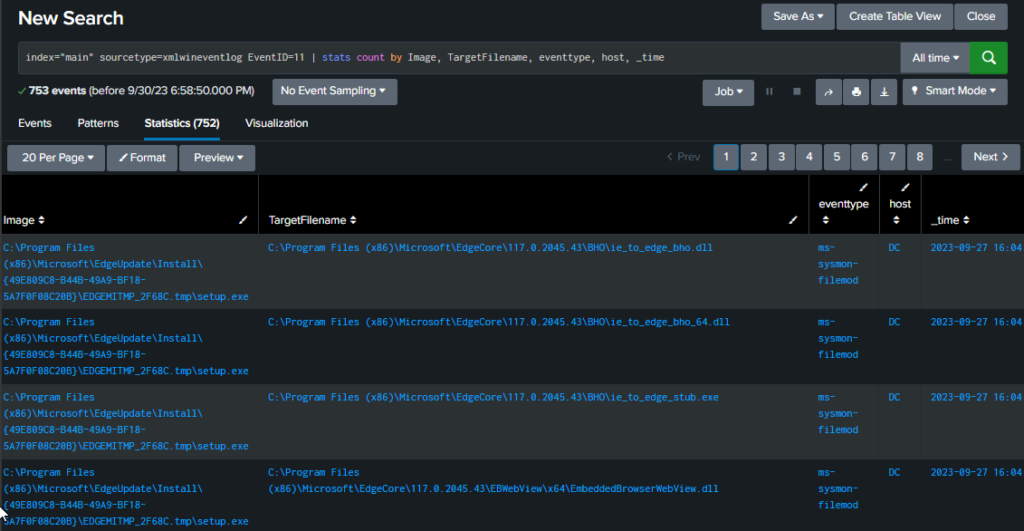
Event ID 11 – File creation or overwritten
The command below will show the path, the file being targeted, if it’s being modified or created, the host, and the time of change/creation.
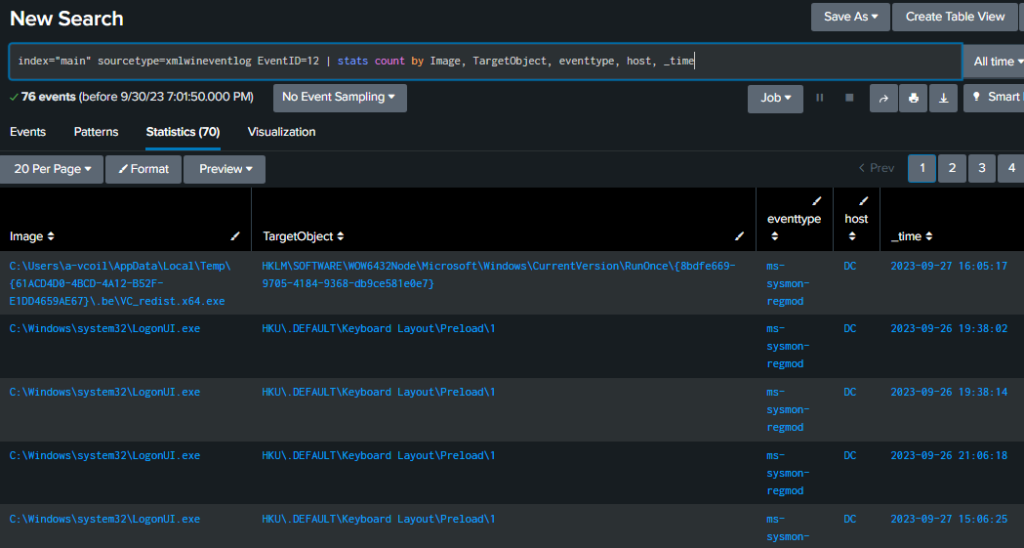
Event ID 12 – Registry Key Object Create and Delete
The command below will pick up on any registry key being created or deleted.
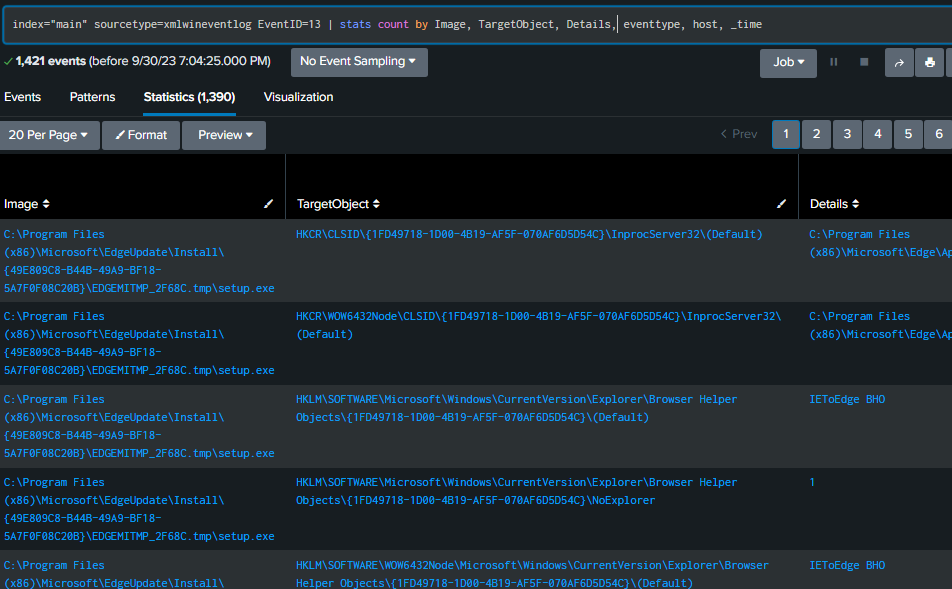
Event ID 13 – Registry Value Set
This Event ID will show the values that are set for a registry key
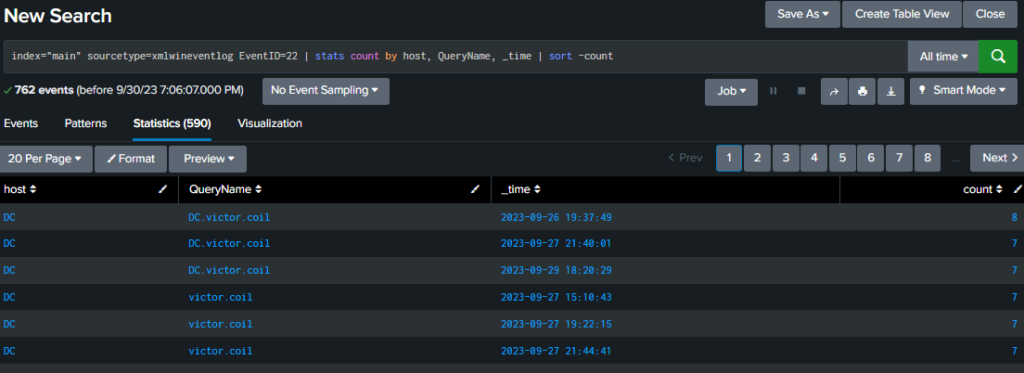
Event ID 22 – DNS Event
The command below will show any DNS events occurring
So what have we done…
– Deployed Splunk Enterprise (SIEM) for Centralized logging
– Enhanced logging using Sysmon
– Deployed Snort Intrusion Detection System (IDS) into the environment
– Forwarded All Logs, including Snort Logs, using Universal Forwarders
This concludes the lab.
